SSH proxy jump: Difference between revisions
mNo edit summary |
|||
| (6 intermediate revisions by the same user not shown) | |||
| Line 8: | Line 8: | ||
The SSH proxy jump will make a connection to the sandbox through XPUB's XVM server. | The SSH proxy jump will make a connection to the sandbox through XPUB's XVM server. | ||
== | ==First make and upload a SSH key for your sandbox user== | ||
You can follow the instructions on this page: [[SSH]] | |||
These steps need to be done on your own computer. | |||
==Configure the SSH proxy jump== | |||
The SSH proxy jump works with a special user (called "jump") on the xvm (the XPUB server). We work with one shared pair of keys for this user: the '''jump user SSH keys'''. Everyone downloads these keys to their local <code>.ssh</code> folder, and the public <code>jump.pub</code> key is installed on the xvm. | |||
To do this, first download the jump keys from Zulip. The keys we use this year (2024/2026) can be found [https://zulip.xpub.nl/#narrow/stream/88-XPUB1/topic/Cereal.20Box.20SSH.20insturctions.3A/near/44170 here]. Save them to the <code>~/.ssh/</code> folder on your laptop (not on the sandbox!): | |||
jump | jump | ||
| Line 24: | Line 32: | ||
Host NAMEOFSANDBOX | Host NAMEOFSANDBOX | ||
Hostname 10.0.0. | Hostname 10.0.0.XX | ||
User USERNAME | User USERNAME | ||
ProxyJump xvm_jump | ProxyJump xvm_jump | ||
| Line 33: | Line 41: | ||
$ ssh NAMEOFSANDBOX | $ ssh NAMEOFSANDBOX | ||
==(for staff) generate and install new jump SSH keys== | |||
We started to work with a new set of keys for the jump user for each year, because passphrases were forgotten, or the keys somehow mysteriously did not work. | |||
So for a new year: | |||
# generate a new pair of keys | |||
# rename them to jump and jump.pub, and share them with the students on zulip | |||
# ssh into xvm, switch to the jump user: $ sudo su jump | |||
# copy one of the lines in /home/jump/.ssh/authorized_keys and add jump.pub | |||
==Uploading files with FTP== | |||
You can use the SSH shortcut from your config file, and SSH key that you generated. | |||
* '''servername''': <code>cerealbox</code> | |||
* '''key''': select <code>id_ed25519</code> | |||
===Cyberduck=== | |||
Install: https://cyberduck.io/ | |||
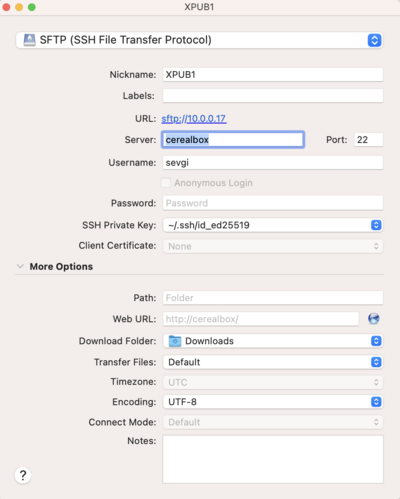
Howto: you can follow this screenshot that Sevgi made: | |||
[[File:Cyberduck-ssh-proxy-jump-setting.png|400px]] | |||
===Winscp=== | |||
Install: https://winscp.net/ | |||
Docs: https://winscp.net/eng/docs/ui_import#openssh_config | |||
Howto: i did not test winscp yet, but it should work in the same way as Cyberduck :fingers_crossed: | |||
===scp=== | |||
(using the terminal) | |||
You can also upload files through the terminal with scp. | |||
I made a short howto page on the wiki: [[Scp|scp]] | |||
==Claudio's notes (⚠ ⚠ to edit)== | ==Claudio's notes (⚠ ⚠ to edit)== | ||
Latest revision as of 12:34, 22 October 2024
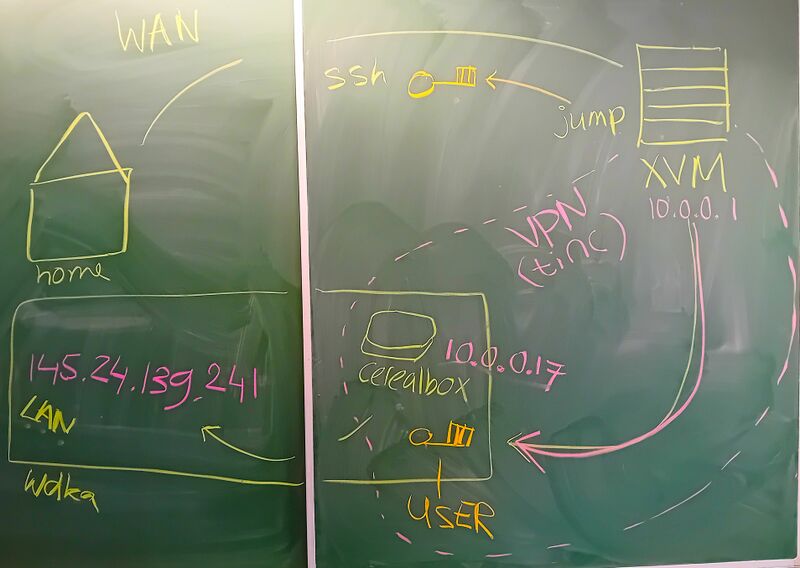
As the collective sandbox servers are hosted from the school, they use a hidden VPN network to connect to the internet, famously known as the HUB.
To be able to SSH to a sandbox server from outside of the school, you can use a SSH proxy jump.
The SSH proxy jump will make a connection to the sandbox through XPUB's XVM server.
First make and upload a SSH key for your sandbox user
You can follow the instructions on this page: SSH
These steps need to be done on your own computer.
Configure the SSH proxy jump
The SSH proxy jump works with a special user (called "jump") on the xvm (the XPUB server). We work with one shared pair of keys for this user: the jump user SSH keys. Everyone downloads these keys to their local .ssh folder, and the public jump.pub key is installed on the xvm.
To do this, first download the jump keys from Zulip. The keys we use this year (2024/2026) can be found here. Save them to the ~/.ssh/ folder on your laptop (not on the sandbox!):
jump jump.pub
Copy the following config file, change the USERNAME to your username, and save it to ~/.ssh/config on your laptop:
Host xvm_jump User jump Hostname 194.61.65.6 Port 2501 Identityfile ~/.ssh/jump Host NAMEOFSANDBOX Hostname 10.0.0.XX User USERNAME ProxyJump xvm_jump Identityfile ~/.ssh/id_ed25519
Now, you should be able to ssh to the sandbox, both from the school and outside the school, with this command:
$ ssh NAMEOFSANDBOX
(for staff) generate and install new jump SSH keys
We started to work with a new set of keys for the jump user for each year, because passphrases were forgotten, or the keys somehow mysteriously did not work.
So for a new year:
- generate a new pair of keys
- rename them to jump and jump.pub, and share them with the students on zulip
- ssh into xvm, switch to the jump user: $ sudo su jump
- copy one of the lines in /home/jump/.ssh/authorized_keys and add jump.pub
Uploading files with FTP
You can use the SSH shortcut from your config file, and SSH key that you generated.
- servername:
cerealbox - key: select
id_ed25519
Cyberduck
Install: https://cyberduck.io/
Howto: you can follow this screenshot that Sevgi made:
Winscp
Install: https://winscp.net/
Docs: https://winscp.net/eng/docs/ui_import#openssh_config
Howto: i did not test winscp yet, but it should work in the same way as Cyberduck :fingers_crossed:
scp
(using the terminal)
You can also upload files through the terminal with scp.
I made a short howto page on the wiki: scp
Claudio's notes (⚠ ⚠ to edit)
When you connect to the sandbox you normally type this in the terminal :
ssh + *yourusername + *sandbox's id address
Inside of the school, this works, you're connecting to the sandbox under the same network, but how does it work from home or from outside of the school's walls in general?
If you're somewhere else you'll have to connect to the XVM (XpubVirtualMachine) server, which is a public server from the school that hosts all the sandboxes (and other things like ...).
The XVM is somewhere, but definitely not in the building. Inside the XVM, you'll log into a public user called "jump" (*representation of jump 🕵), jump is part of a super secret connection that is not accessible to the broader "public", through this connection (VPN)