Why Map? The Techno-epistemological outlook
Author: Richard Rogers
The essay concerns what kind of commitments researchers and designers take on when they map social networks. More specifically, it takes up what may happen when social network researchers slope towards intelligence work.
Introduction: Maps that organize networks
Frontline, the American PBS investigative news program, aired a show in September 2002 that in many respects summarizes the public drama surrounding social network mapping by intelligence agencies and by amateurs. It is a story - a parable in fact - of the former FBI agent, John O'Neill - 'the man who knew,' but wasn't listened to.[1] He now tours, giving speeches with sentences as: "How much more successful could we all be if we really knew what our agencies really knew?" I briefly would like to take up this question.
Valdis Krebs also knows (and has put it on the Web). He "used public information, from major newspapers on the WWW, to uncover the terrorist networks."[2] His map is among a growing number "connecting the dots" between individuals involved in the Al Qaeda network, and events going back to the 1980s. Once the dots are connected, Osama Bin Laden is centrally positioned (see figure one).
Aired on the anniversary of the terrorist attacks on the U.S., the PBS program prompted journalists to probe deeper into the study of networks by professionals and amateurs alike. One headline read: "Network science could provide patriot gains" (Dallas Morning News, 9 September 2002). In the growing popular literature, O'Neill, Krebs and others are among those cited as knowing the network (also by having mapped it).
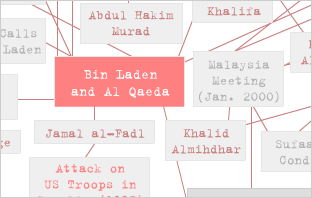
Historically non-technical networks have been associated with organized crime, terrorists as well as the old boys from the Ivy League and beyond. Indeed, to some, social network maps have explanatory power, often a postiori.[3] Famously, the new media piece, theyrule.net by Josh On provocatively visualizes social connections among corporate board members (old boys). Bill Clinton's choice of Vern Jordan to find Monica Lewinsky a job has been thought in terms of his position in another network (mapping exercise) of corporate board members of America's largest corporations.[4] Jordan, it was found, was the most central figure at the time, only 3 handshakes away from all top boards.
One could argue that it has been the lack of legibility of these networks as well as questions about accountability for actions that have prompted analytical and political efforts to 'map the networks'. I would like to argue, rather, that in the above cases it is the format of the map that (dramatically) organizes these networks.
Saying maps organize networks could be interpreted as taking the constructivist position that there is only a network when there is its representation in the form of a map (or graph, technically speaking) - one that subsequently cannot be disentangled from the real. (As with the map-territory problem, it would be difficult to think of the network independent of its map. It's still difficult to navigate it, however, but it has its navigators built in - the example of Vern Jordan.) I would like to argue, however, that mapping social networks reveals commitments to an outlook that may be called a techno-epistemology, a way of coming to know and making particular claims only with a technological apparatus that desires to grow to satisfy its cravings for 'really knowing' and, especially 'really knowing what our' intelligence also knows or should know. I would like to describe this outlook in terms of how it aligns itself with a particular commitment to deep information as well as a technological project.
The techno-epistemological outlook: Tracking and tracing
Most importantly, one can only really know when one has technology of a particular kind. It is an apparatus that collects and analyzes information using particular techniques. The information-gathering apparatus, firstly, would be a step up from tracking to tracing. Often the two terms are not clearly distinguished. Tracking concerns recording events, such as arrivals and departures of a package along a route that includes a warehousing event, a truck-loading event, a customs arrival event, a customs clearance event, etc. A package is tracked by recording its arrival and departure at given points along a route. (The route may not always be the same, but there is a route made up of events that may be tracked, and subsequently mapped.) Tracing, however, should not be confused with connecting the dots of events. Rather, tracing is movement monitoring, an effort to record the full trajectory of the package's journey. For example, one could imagine tracing eventually being accomplished by an embedded receiver in a package (or a chip implanted in your cat, or in your mobile phone). The location is always either to be determined (which is not quite tracing), or actually being determined through the monitoring of the recording (which is tracing). The expression "put a tracer on it" (watch its movement) is thus technically distinguished from "track it down" (access recorded events to locate it or its last whereabouts). Tracing is far superior in the techno-epistemological outlook I wish to describe. When Greenpeace USA quietly affixes a 'falcon tracker' to a logging truck, captures the movement trace though geographical positioning and uses a geographical information system to show the logging truck's route (on a map of dirt roads through protected old growth forests, for example), their work approaches tracing. The result is a map of the loggers' movements, and may be used as evidence to make claims.
Secondly, in the techno-epistemological outlook, one understands the lines between nodes in networks as social connections in two senses: 'tracked' history (various shared experiences that make nodes into "old boys" or associates) as well as the intersection of preferably traced movements (trajectory crossings). A mapping program ideally would be able to show both views as layers (or mode switches) that may be turned on and off. A user may say: "I notice that these three individuals have crossed paths frequently. Show me whether they have historical connections (whether they are old boys)." Being shown related nodes, with historical connections, may prompt analysts to ask to put a tracer on them, too. So history and trajectory tracing feed upon each other in the data we seek (and the technology developed to seek it) according to the techno-epistemological outlook.
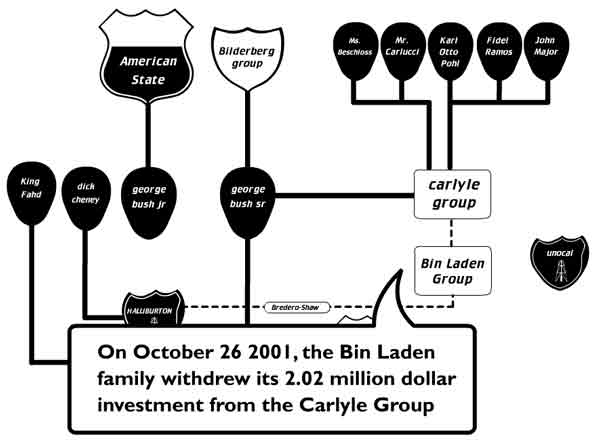
Thirdly, it is important to know whether the networks are actually in operation. The shortcoming of much social network analysis is to assume there exists a network structure that itself enables claims without further probing network activity. In the techno-epistemological outlook described here, the question of network operation is fundamental. One way of describing the question is to look at one of the maps made by Bureau d'etudes or by Josh On.[5] (See also figure two.) One could ask, what if we introduced a suitcase of money into this structure? Which path might it take? With path shown, would we have to redraw the map, perhaps fade out some nodes or remove them? Once the map is redrawn continually, 'structure' (in the historical sense) may or may not emerge. We may or may not have history 'layers' to turn on an off.
Fourthly, as networks are historical as well as (ideally) physical movement lines socially connecting individuals, to understand whether they actually are functioning and operating as 'networks' (in our techno-epistemological sense) requires more information than is 'publicly available'. To know how the dots connect (beyond event recording), whether the trace is meaningful (beyond movement recording), with or without switching to history mode, one would like to have activity detail, from the dry to the salacious. A commitment to network knowledge as described would include a desire to read the transcripts of conversations in restaurants and kitchens as well as on hotel grounds and airplanes - in fact, preferably all conversations at significant junctions in the movement trace that traditionally have been deemed difficult to record (and thus preferred places for nodes to speak).
Fifth, with the conversation transcripts in hand comes the concern put forward in publicly available sources (e.g., newspapers) that there are not enough readers. Reading is often thought impossible given voluminous data, so concomitant conversation mapping could be employed. Specially, an analysis is sought of plans and promises, preferably without pre-defined dictionaries for textual and semantic mapping of particular key words, for the nodes may speak in code. Often the Internet, if I may, alleges that it is circulating these lists of words ('dictionaries,' technically speaking) that would flag email as well as conversations as worthy of reading by intelligence.
Sixth, such a commitment to conversational knowledge would lead directly to the need for action mapping (the money suitcase example). To ascertain whether plans and promises were acted upon, additional data sets may be called upon. Currently, financial transaction mapping, from credit card transactions to bank transfers, is the preferred means to see whether or not the network is operational financially. These means alone would not suffice in our techno-epistemological outlook.
To summarize thus far, with the commitment to map from a social network point of view comes a commitment to seek knowledge not only of the old boy history and path-crossing, but also of the extent to which the network is operating in other senses, too. Financial transaction mapping, however, relies on tracking technology (recording of the event of a transaction), instead of tracing technology. Tracing technology, for example, would have a receiver embedded in an attaché case. To trace properly would require tagged cases as well as tagged currency, for then we would know when "money is changing hands".
In our techno-epistemology, committed network analysts would not believe that networks only have a structure (based on old boy history), within which frequent path-crossing would constitute its current configuration, and perhaps its 'structure'. Rather, a dedication to network activity measures is required.
The commitment to knowing what they know
The first step is a realization that we do not know what the intelligence know, but we may think which data sets as well as means of analysis and visualization they are using to support their claims. So, to know what they know, we first attempt to collect the same data. The argument above concerned the data we may think we need in order to know what they know.
The sad fact of the matter is that our data appear poorer, or seem to be (we do not know for certain). With this realization come two possible avenues. The first is that the decision is taken, often on principle, to use only publicly available information. Publicly available information has both a benefit as well as a flaw. The benefit is that, later, the claim can be made that it was out there all the time. Anyone could have known, intelligence should have known, and their not knowing reveals a level of incompetence and/or larger forces asking for it not to be pieced together in that way. These are resources for story-making, including PBS TV shows, where maps eventually be screened. The flaw is that maybe they know that as well, and have discounted it owing to better data. Nevertheless, we shall work with what we have, for there is software (and important geo-political matters at hand).
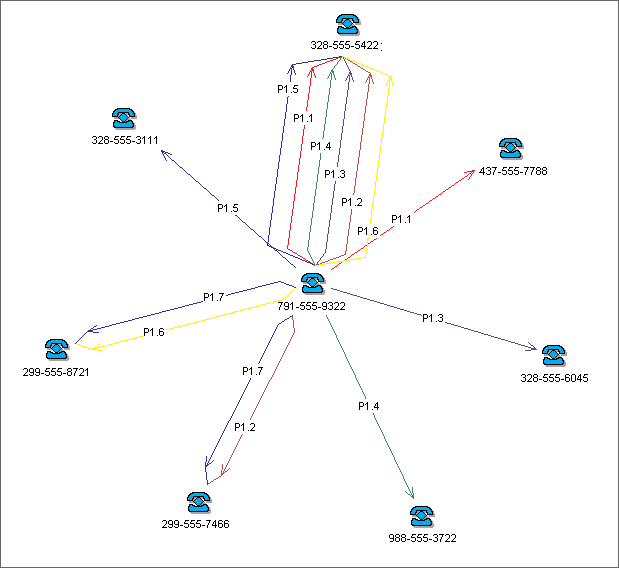
The proper analyst would employ analytical and visualization software approximating theirs. The packages that are commercially available and advertised as used by the police appear attractive (see figure three). It is precisely here, in the sample screens, the demo and the subsequent experience with the package itself, that excitement is generated for particular data collection. Questions immediately arise. Are we able to obtain those records (e.g., phone call data) that would neatly fit into these fields here, in our database, so as to make an image like that one there?
In terms of our output, we may have a workaround for a particular problem confronting positivist undertakings like mapping. In ours and theirs, there is a tendency to erase the back-end, i.e., both the data collection as well as analysis - not only the decisions but also the touch-up's. In positivist science (where mapping has had its home) one often does not allow that. Rather, one strives to verify through reproduction. This may be impossible, given limited access to their data, their instruments, their software. If we are to map properly, we cannot discount our need for positivism owing to the lack of knowledge about the data, the instruments, the software. We could rely, however, on the phrase 'publicly available information,' for that may take the heat off for a moment whilst we make our map. But normally this trick is not pulled; rather, the accompanying paper is fully referenced (more stringently than even the Chicago Manual of Style requires), and the journalist names, newspaper article titles, newspapers, dates as well as page numbers are all given.[6] The display of scientism (journal-making, society formation, conference meetings, heavy referencing), the science sociologists once pointed out, is found across non-academic 'science'.
With paper and map, the far more important question is the extent to which the invitation into the symbolic world is accepted, and the subsequent discussions only revolve around interpretation. This is beyond the techno-epistemological outlook I wish to describe, beyond the realization that we do not know what they know, but would like to think we can approximate the data collection (or decide on principle to use the publicly available) as well as the stunning output. The question is, how successful are the maps (as an information format) in organizing the networks as networks? If the nodes and connections are out there, and we have captured them, can we finally get everybody into a design discussion?
Biography
Richard Rogers is Director of the Govcom.org Foundation, Amsterdam. He is also Assistant Professor in Media Studies at the University of Amsterdam, and recurrent Visiting Professor in the Philosophy and Social Study of Science at the University of Vienna.
Web sites
- http://www.govcom.org
- http://www.issuenetwork.org
- http://www.issuecrawler.net (request account)
- http://www.infoid.org
- http://www.viagratool.org
Acknowledgements
This piece was inspired by the Tactical Cartography session at the Next Five Minutes Tactical Media Festival, Amsterdam, September 2003. The session included Brian Holmes and Bureau d'Etude. Josh On could not attend. The piece benefited from discussions with Jodi Dean and Noortje Marres. I also would like to thank Matthew Fuller for commentary.
Notes
This essay was commissioned by Media Design Research, Piet Zwart Institute, Willem de Kooning Academy Hogeschool Rotterdam. http://pzwart.wdka.hro.nl/
1 http://www.pbs.org/wgbh/pages/frontline/shows/knew/view/, accessed on 7 December 2003.
2 See Valdis Krebs's page describing the work at http://www.orgnet.com/hijackers.html, accessed on 7 December 2003.
3 See also the map by Mark Lombardi, inserted in Cabinet Magazine 2, Spring 2001, entitled "George W. Bush, Harken Energy, and Jackson Stephens."
4 Albert-Laszlo Barabasi, Linked, Cambridge, MA: Perseus, 2002, 202-205.
5 For maps by Bureau d'Etude, see http://utangente.free.fr. Josh On's famous piece, based on 2001 corporate board member data, is available at http://www.theyrule.net. A data refresh is scheduled for 2004.
6 Valdis Krebs, "Mapping Networks of Terrorist Cells," Connections, 24, 3, 2002, 24-52.
Originally published at: http://pzwart.wdka.hro.nl/mdr/pubsfolder/whymap/
