User:Ssstephen/Reading/Steganography of VoIP streams
US Department of Defence specifies that any covert channel with bandwidth higher than 100 bps must be considered insecure for average security requirements. Moreover for high security requirements it should not exceed 1 bps
Covert is essentially insecure, at a certain scale? Security has to be sacrificed for covertness.
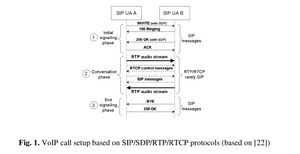
VoIP is a real-time service that enables voice conversations through IP networks. It is possible to offer IP telephony due to four main groups of protocols: a. Signalling protocols that allow to create, modify, and terminate connections between the calling parties – currently the most popular are SIP [6], H.323 [7], and H.248/Megaco [8], b. Transport protocols – the most important one is RTP [5], which provides end-toend network transport functions suitable for applications transmitting real-time audio. RTP is used in conjunction with UDP (or rarely TCP) for transport of digital voice stream, c. Speech codecs e.g. G.711, G.729, G.723.1 that allow to compress/decompress digitalized human voice and prepare it for transmitting in IP networks. d. Other supplementary protocols like RTCP [5], SDP [9], or RSVP etc. that complete VoIP functionality. For purposes of this paper we explain the role of RTCP protocol. RTCP is a control protocol for RTP and it is designed to monitor the Quality of Service parameters and to convey information about the participants in an on-going session.
Before you can have a conversation (RTP) you need the signalling phase (SIP). There is a difference between a caller and a callee. The caller needs something from the conversation and is in the driving seat. The callee is subjected to the conversation, are they able to leave? ("I don't know, you called me!"). Is communication ever equal? Are there protocols that can make it more equal? ("I will be at this IP address at this time if you want to chat. I understand if you don't want that or are not ready.")
How are text messages sent from apps like WhatsApp, Telegram, Signal?
the available steganographic techniques for this phase of the call include: • IP/UDP/TCP/RTP protocols steganography in network and transport layer of TCP/IP stack, • RTCP protocol steganography in application layer of TCP/IP stack, • Audio watermarking (e.g. LSB, QIM, DSSS, FHSS, Echo hiding) in application layer of TCP/IP stack, • Codec SID frames steganography in application layer of TCP/IP stack, • Intentionally delayed audio packets steganography in application layer of TCP/IP stack, • Medium dependent steganographic techniques like HICCUPS [15] for VoWLAN (Voice over Wireless LAN) specific environment in data link layer of TCP/IP stack.)
Wow that's a lot of ways to send a secret message. Also don't forget about the PNG thing with cropping and the data staying in the file.
It is also worth noting that RTCP messages are based on IP/UDP protocols, so additionally, for one RTCP packet, both protocols can be used for covert transmission.
The layered nature of communication seems to in itself provide opportunities for additional or alternative messages. Like how using line breaks in text allows for the acrostic poem, all formatting and encoding paradigms can be opportunities for communication.
The primary application of audio watermarking was to preserve copyrights and/or intellectual properties called DRM (Digital Right Management). However, this technique can be also used to create effective covert channel inside a digital content.
Could audio-watermarking be used for piracy? Is that a joke worth making? Sounds complicated.
For VoIP service when highly delayed packet reaches the receiver it is recognized as lost and then discarded. We can use this feature to create new steganographic technique. If we are able to add enough delay to the certain packets at the transmitter side they will not be used for conversation reconstruction, and we can utilize their payloads for covert communication.
Cool. But the idea that a message isn't valid unless it arrives on time is important in a more general sense, urgency is always a factor in communication. Even archives have urgency.
Proposed steganographic method has certain advantages. Most of all, although it is an application layer steganography technique, it is less complex than e.g. most audio steganography algorithms and the achieved bandwidth is comparable or even higher.
Tres cool.
t the most important steganographic method in VoIP communication experiment is IP/UDP/RTP protocols steganography, while it provides over 96% of achieved covert bandwidth value.
Other methods seem like a waste of time compared to this, unless you think you will be caught.