User:Dave Young/Thematic Project 1
Link to Fruitsalad
Covert Networks
Random Notes
Number stations: Radio networks that broadcast codes, popular theories are that they are used for espionage purposes or for drug smuggling.
One-time pads: indecipherable coding systems for eavesdroppers. Often used to encrypt number station broadcasts.
Automated reel-to-reel tape recorders: timed to play broadcasts at certain times of the day. Occasionally they "fail", and broadcast the code at an incorrect speed, or broadcast the wrong code entirely.
Re-watch: The Conversation by Francis Ford-Coppola - Listening/Paranoia/Cold War/Nixon/Espionage.
Radio as a filesharing medium? Using mplayer to send data as raw audio over a radio network.
The Fruitsalad Enigma
Continuing with the idea of covert networks and cryptography, I have begun working on an experimental encryption tool (alpha stages at the moment) codenamed The Fruitsalad Enigma, and returns the encoded message as a list of fruit (some exotic variants included). The encryption algorithm, as the name suggests, is inspired by the Enigma machine - used during World War II and cracked by a collaborative effort that included the Polish resistance and a team at Bletchley Park (Britain's wartime decryption centre). Like the Enigma, it employs the use of "rotors" (albeit conceptually rather than mechanically) which alters the encryption algorithm for each character in the message.
While watching a documentary on tv about World War 2 one Saturday night instead of being out socialising (I was ill, or something) I became curious about how networks can become superimposed on top of each other: for example Hitler used a number of encryption machines to encode messages of varying confidentiality, with each encryption machine having its own "layers" of nodes placed throughout Europe. Each layer is designed to exclude/include different groups of people - some encrypted networks were deliberately allowed to be broken to fool the enemy, whereas others such as the Lorenz network were used for the most important and decisive messages and had a very limited nodal pool.
The idea arose out of the many discussions during the thematic project seminars about data, privacy, and social networks. Thinking that facebook's advertising algorithms were content-dependent, I thought that flooding your facebook profile messages with status updates about fruit would skew the advertising data facebook collects about you. I've since discovered that the advertising algorithms are slightly more meta, and in fact do not depend on what's on your "wall" (as far as I understand it at least, facebook seems happy to remain ambiguous about such issues at times). In any case, a browser plugin of the Fruitsalad Enigma could provide an encryption and decryption service would allow the user to use the "shopping mall/private space" of Facebook while limiting the amount of information Facebook's data sniffers can gather on them by giving them a junk list of fruit, so at least they think the user is not prone to scurvy.
Encryption automatically assumes the presence of "the other", that is, the presence of the "eavesdropper" who should be excluded from the communication - without the paranoid fantasy of the eavesdropper, there is no need for encryption. It is my intention with this piece to at least symbolically raise the issue of the "eavesdropper", and render lucid the quiet automated listeners that feedback your information in the form of sidebar advertisements and suggested actions. Hopefully the playfulness of the encryption method will encourage those in the user's network to become curious enough to look into the subject themselves.
Blah-Blah
I'm using this "project" as a way of learning more about string operations in python. I'm also curious about using python alongside bash, perhaps building a terminal-based UI with 'dialog' so the user can input their text, providing a suitably anachronistic aesthetic for an encryption/decryption tool :)
A point of interest for me is that with the original Enigma, no encoded letter every referred to itself (ie the letter 'a' was never encrypted as 'a') - this pattern was picked up by the codebreakers and was an important feature that led to its eventual decryption. The idea of hiding text in plain sight is also interesting to me - disguising an encrypted message as another piece of text entirely.
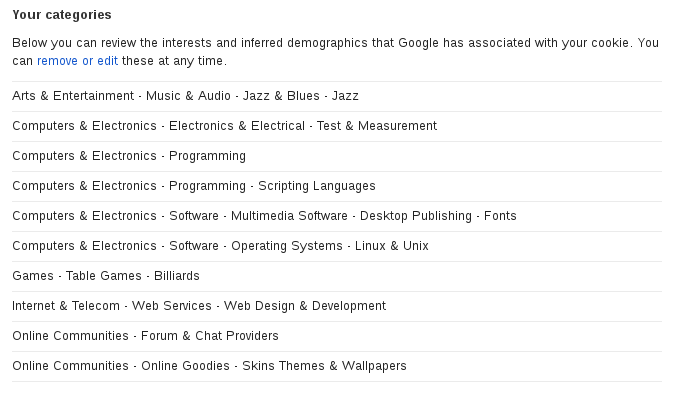
What Do Google Know?
What Next?
- Encryption/Decryption Python Scripts - Completed
- Encryption/Decryption Website - In Progress!
- Javascript plugin for Facebook - Currently researching. If anybody more adept in javascript than myself (that means everybody) want to assist, please do!
For the future:
- A Fruitsalad Enigma font?
- Branded T-Shirts and hats.
A SECRET CODE
PEACH BLACKBERRY PEAR MANGO MANDARIN LEMON STRAWBERRY APPLE DRAGONFRUIT BANANA TANGERINE MANGO CRANBERRY PASSIONFRUIT RASPBERRY PAPAYA DRAGONFRUIT AVOCADO PEAR PINEAPPLE CRANBERRY LEMON CRANBERRY BANANA ORANGE GRAPE GRAPEFRUIT POMEGRANATE MANGO KIWI GRAPEFRUIT APPLE COCONUT STRAWBERRY VANILLA
Source
Source code will be released when some loose ends are tidied up, or if somebody manages to crack the above encrypted message before then :)