User:Andre Castro/2/semina aymeric/blog/spamLanguage
spam language
During past week it became clear that rather than adding layers to the existing spam, or producing spam myself, I want to look at its peculiarities and why it fascinates me. In other words I want to elevate the value of spam. Although the challenge can be tackled in a variety of ways, as many as there are explanation as to why spam is fascinating, I need to find an angle from which to approach it. I have decided to focus on spam's use of language, which in itself is still quite broad scope, so I am trying currently to work the following points:
- The presence of a common structure underpinning spam messages (one for each of its given sub-genres);
- The array of stock characters featured in them;
- The networked nature of the texts;
In order to provide a more solid base for my research I will concentrate exclusively on the 419 Advance Fee Fraud emails, as the sub-genres of spam are too many and of quite a distinct nature, to allow us to analyze the whole field with any given depth.
Common structure
By doing a close reading of a few 419s emails I was able to identify a few plot events that seem to be present in each of the emails.
Similarly to Vladimir Propp's approach in the Morphology of the Folktale, in defining the plot events or functions I tried to focus on what action is performed, and not on who or how it is performed, the action is a constant, yet it can be actualized by many characters in various ways.
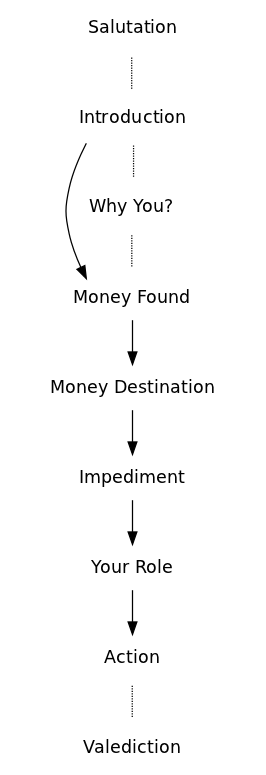
So far I have isolated the following nine functions:
Salutation: The writer begins by saluting the reader. Often only with a plain "hi", others times the writer might already try to establish a bound with the reader using a more intimate approach "Hello Dearest One" writes Alima Kipkalya.
Why you?: This function, while not central to the plot, tries to justify why is the reader receiving such email. Often the writer refers to her desperate situation, to which the reader can be a way out. This function often appears after the introduction.
Introduction: The writer introduces herself. This is a pivotal moment for the narrative, since who the writer happens to be will dictated how the following functions are enacted. Possible characters found so far featuring the role of the writer were a banker, a family member of a state's person, a soldier, a rich but ill widow.
Money Origin: The reader is told about the sum of money that took the writer to contact her. The money origin will depend on who is writing the email. The banker comes across money from a deceased client; the relative to the state's person inherits his fortune; the soldier finds money during an armed conflict; the terminally ill woman inherits her deceased husband fortune.
Money Destination: The writer describes the destination she wants to give to the money. This function is also dependent with who the writer is, if it happens to be an ill woman she will want to give the money to charity, the soldier on the other hands wants to keep it for himself.
Impediment: An impediment doesn't allow the money to remain with the writer and she informs the reader as why she isn't able to keep the money. Consequently she needs the reader's cooperation. Like with the Money Destination the impediment is not always clearly stated. Yet, it continues to be dependent on the who the writer is (Introduction). In the particular case of the banker Peter Hayman, it is hard to tell why can't he keep the funds from the deceased client; the daughter cannot checkout the money from the bank until she finds a husband or trustee, the soldier cannot keep the money as it is illegal, the widow is on the verge of death.
Your role: The reader is informed as what her role will be within the portrayed scenario. The reader also learns about her reward for helping out: "It is my intention to compensate you with 30% of the total money for your services", states Alima Kipkalya Kones.
Action The receiver is urged to confirm her interest in the proposal by replying to the email and often by proving information on herself. She might be given instruction as what to how to act upon the writer's instruction.
Valediction concludes the email. It must be in accordance to whom the writer happens to be. The banker simply writes "Yours Faithfully", followed by his bank contact; the soldier with "Yours in Service"; and the devoted christian widow with "May the Grace of our Lord Jesus Christ,the love of God,and the fellowship of the Holy Spirit be with you and your family."
Essentially the functions follow the same sequence throughout the studied emails, yet it is common for these plots to employ a smaller amount of functions than the entire array of identified ones. Functions also seem to be interrelated, particularly in case of the introduction, since the way in which a function is instantiated will have repercussions on to how the following functions are concretized. Currently I am undergoing the isolation of functions found emails, these can be found at http://pzwart3.wdka.hro.nl/django/acastro/collect_spam/categories/
Stock characters
Another strong aspect I have noticed is the employment of a limited amount of stock characters featuring as the writer of the email: the banker, the American or British soldier, the young woman (relative to a state's person), the rich but sick widow. It is almost without exception one of these characters who appears as the writer of the 419s, who is given his singularity, through variables such as his name, country of origin, age. Yet the character remains essentially the same, behaving in the same predictable manner, making the same type of request, appealing to the same type of feelings the in the reader.
We could easily create a chart containing the defining characteristics of a stock character, its constants.
biography: mode of address: appealing to fellings: impediment for getting to the money: request to the reader:
The most extreme case of stock characters (ab)use I came across, was a character under the surname of Kones. Miss Kones is the daughter of a Nigerian politician, who died on a plane accident; the daughter inherited her father's fortune, but is only allowed to checkout the money when married or has found a trustee; and to complicate matters both her uncle and stepmother are trying to get hold of the fathers fortune. Miss Kones writes under various of first names: Susan, Joy, Alima, Cindy, etc. The story is always the same, and Miss Kones appeals to the reader's greed for money, but also to those wanting to be seduced by a young woman. This multiplication of one stock characters into a myriad of slightly different variations is common, yet the reuse of the same character's name and history, in is particular to this example.
networked texts
If we stick to the example of Miss Kones and look at the various existing versions of the same story. We easily see the extreme appropriation this story undergoes. Many chunks of texts are simply copied from one version to another, and it is common for a great deal of it to be left intact, apart from a few small changes. But what are those changes, and is the chunks that remain untouched? And how could one draw attention to the repetition of patterns throughout the various versions?
I made small experiment for trying to materialize the reappearing patterns across a few versions of Miss Kones emails. I asked a few friends to read the emails, one text per person. I overlaid the various readings and, while preserving each text's original sequence, tried to sync the sentences common to more than one email. When reading the same, repeated material, the voices join into a chorus effect, emphasizing what is being read, whiles when the material diverges it becomes hard to apprehend all the streams, or even follow one.
http://pzwart3.wdka.hro.nl/~acastro/stuff/Master_17_02_A.ogg
(In this context it becomes difficult to talk about an origin. Which one of these versions is the source? How could we get to the source? )
I am not sure of how will I carry on developing this exploration of patterns, repetition, and differences. Perhaps I could reduce my unit of comparison from sentences sequences, to sequences of two or three words, and try to materialize the reappearance of those shorter units in the sequence. Let's imagine I take one of the stock characters and make recordings of the readings of a few of his emails, each with a different voice. I can then arrange those versions into variety of patterns, moving from larger units of comparison to smaller ones.
The material could perhaps be arranged in the following sequence:
1) CHASE - We here the different voices reading the same text parts from different emails. Overlap of voices is little; Soldier 1 introduction Money Origin Money Destination Soldier 2 introduction Money Origin Money Destination Soldier 3 introduction Money Origin Money Destination 2) CHORUS - the repeating phrases appear sync Soldier 1 Reapeated Sentence #1 ...## diverging voices ##... Reapeated Sentence #2 ...## or silence #... Reapeated Sentence #3 Soldier 2 Reapeated Sentence #1 ...## diverging voices ##... Reapeated Sentence #2 ...## or silence #... Reapeated Sentence #3 Soldier 3 Reapeated Sentence #1 ...## diverging voices ##... Reapeated Sentence #2 ...## or silence #... Reapeated Sentence #3 3) PARTICLES - sequences of two of three words that reappear are juxtaposed Soldier 1 Particle #1 Particle #2 Particle #3 Particle #3 Soldier 2 Particle #1 Particle #2 Particle #3 Soldier 3 Particle #1 Particle #2 Particle #3
Perhaps this re-arrangement of spam material could be performed live by singers/actors.
(I am thinking that an important resource in the sorting of this material would be to have time-stamps for each word. So I'd have a sound file and a subtitle file (with a word per entry that would allow me to ask for a given sequence of words to be played.)