Interfacing the law project proposal Zalan Szakacs: Difference between revisions
| Line 58: | Line 58: | ||
=Steps to take= | =Steps to take= | ||
→ | → Writing the source code of creating 3D shapes based on metadata | ||
<br> | |||
→ Writing the source code of 3D steganography (MD5 hash or sim hash), which would decrypt informations in 3D shapes | |||
<br> | |||
→ Writing the source code for code generator | |||
<br> | |||
→ 3D printing + 3D scanning testing | |||
<br> | |||
→ WebGL interface to create | |||
<br> | |||
→ Testphase of the website + 3D printing + 3D scanning | |||
<br> | |||
→ Project documentation | |||
<br> | |||
→ Presentation preparation | |||
<br> | |||
=Resources= | =Resources= | ||
[https://ieeexplore.ieee.org/document/8089350/authors A High-Capacity 3D Steganography Algorithm With Adjustable Distortion] | [https://ieeexplore.ieee.org/document/8089350/authors A High-Capacity 3D Steganography Algorithm With Adjustable Distortion] | ||
Revision as of 20:34, 14 May 2018
Research about 3D Steganography
Redesigns of the 3D printed gun
3D Steganography talk by Dennis de Bel
3D Steganography 3D printing project by Dennis de Bel
Pattern based 3D image Steganography
Embedding data in 3D models
A High Capacity 3D Steganography Algorithm
A High-Capacity Data Hiding Method for Polygonal Meshes?
Object Steganography, Noah Feehan (2012)
Disarming Corruptor
pirating 3d prints by listening to the printer
Questions to think about
- Which part of the collection should be hidden? Why?
- How to link with the X-Lib?
- Based on which metadata variables are the shapes created?
- Which feature would transform the 3D generated shapes into 3D printable files?
- Who is using it? Only PZ?
- What is the most important features?
- Where would be situated? local? networked? physical space?
- When would it be available? Temporary? Always?
Project proposal
- 3D steganography version of the library
- 3D shapes printed with the 3D printer from the school
- circumvention of censorship
- simhash process + MD5 Hash - showing the visability in the 3D shape (shows the evolution of the collection)
- with a 3D scanner it will be possible to access the collection of the library again
- mirroring and visualising the collection
- alternative way of looking at the collection
- compression
- time capture in 3D file
What would be an alternative way of looking at the collection?
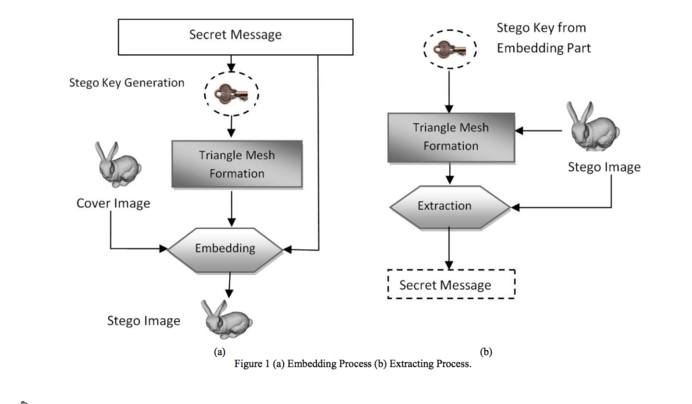
An additional feature of the X-Lib is the 3D steganography library based on WebGL. Parts of the collection such as links or PDF's are transformed based on the metadata into 3D shapes. Through a stenography script the source link (simhash or MD5 hash) will be decrypted inside of the 3D shape. During the transformation phase the interface generates an encryption code as well. The 3D generated shape will be possible to 3D print as well. With help of a 3D scanner the 3D shape could be scanned and with the encryption code the original content would be revealed. This project explores new possibilities of mirroring, visualising and circumventing of censorship of digital libraries in physical manner.
Steps to take
→ Writing the source code of creating 3D shapes based on metadata
→ Writing the source code of 3D steganography (MD5 hash or sim hash), which would decrypt informations in 3D shapes
→ Writing the source code for code generator
→ 3D printing + 3D scanning testing
→ WebGL interface to create
→ Testphase of the website + 3D printing + 3D scanning
→ Project documentation
→ Presentation preparation
Resources
A High-Capacity 3D Steganography Algorithm With Adjustable Distortion
3D image watermarking
Watermarking of 3D Meshes using Matlab