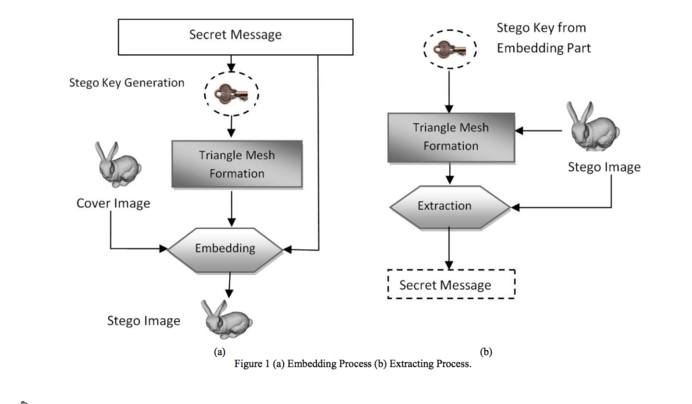
Interfacing the law project proposal Zalan Szakacs: Difference between revisions
No edit summary |
|||
| Line 17: | Line 17: | ||
[https://www.researchgate.net/publication/256104122_Pattern_based_3D_image_Steganography Pattern based 3D image Steganography] | [https://www.researchgate.net/publication/256104122_Pattern_based_3D_image_Steganography Pattern based 3D image Steganography] | ||
<br> | <br> | ||
[https://www.researchgate.net/publication/225126087_Embedding_data_in_3D_models?enrichId=rgreq-f6b8b648a1fdffc4c699d364cdfc8a2b-XXX&enrichSource=Y292ZXJQYWdlOzIyNTEyNjA4NztBUzoxMDI5NDY0OTg5NDA5MzNAMTQwMTU1NTc2NzM0Mw%3D%3D&el=1_x_3&_esc=publicationCoverPdf Embedding data in 3D models] | |||
[http://graphics.csie.ncku.edu.tw/Paper_Video/TVCG_Data_Hinding/TVCG_Data_Hinding_accepted_2208_06.pdf A High Capacity 3D Steganography Algorithm] | [http://graphics.csie.ncku.edu.tw/Paper_Video/TVCG_Data_Hinding/TVCG_Data_Hinding_accepted_2208_06.pdf A High Capacity 3D Steganography Algorithm] | ||
<br> | <br> | ||
Revision as of 23:16, 13 May 2018
Research about 3D Steganography
Redesigns of the 3D printed gun
3D Steganography talk by Dennis de Bel
3D Steganography 3D printing project by Dennis de Bel
Pattern based 3D image Steganography
Embedding data in 3D models
A High Capacity 3D Steganography Algorithm
A High-Capacity Data Hiding Method for Polygonal Meshes?
Object Steganography, Noah Feehan (2012)
Disarming Corruptor
Project proposal
- 3D steganography version of the library
- 3D shapes printed with the 3D printer from the school
- circumvention of censorship
- simhash process MD5 Hash - showing the visability in the 3D shape (shows the evolution of the collection)
- with a 3D scanner it will be possible to access the collection of the library again
- mirroring and visualising the collection
- alternative way of looking at the collection
- compression
- time capture in 3D file