Reverse ssh tunnel: Difference between revisions
Andre Castro (talk | contribs) (Created page with " To access a local machine, behind a firewall, without a public IP, we can use a reserve ssh tunnel - a poor man's VPN. The steps are the following: '''From the machine you...") |
Andre Castro (talk | contribs) No edit summary |
||
| Line 5: | Line 5: | ||
'''From the machine you want to access (local machine)''', create an ssh tunnel to a '''publicly accessible server (remote machine)''', like pzwart1: | '''From the machine you want to access (local machine)''', create an ssh tunnel to a '''publicly accessible server (remote machine)''', like pzwart1: | ||
<source lang="bash"> | |||
ssh -N -T -R 2222:localhost:22 username@pzwart1.wdka.hro.nl | |||
</source> | |||
This command establish a tunnel with a <code>-R</code> remote entry point between the local machine and the remote machine . | This command establish a tunnel with a <code>-R</code> remote entry point between the local machine and the remote machine . | ||
| Line 15: | Line 17: | ||
To access the localhost, from any where, all you need to do is login to the remote, as you normally do: | To access the localhost, from any where, all you need to do is login to the remote, as you normally do: | ||
<source lang="bash"> | |||
ssh username@pzwart1.wdka.hro.nl | |||
</source> | |||
Once inside the remote, you simply login to its own localhost, but on port 2222, which will reach "localhost port 22", which is is our | Once inside the remote, you simply login to its own localhost, but on port 2222, which will reach "localhost port 22", which is is our | ||
<source lang="bash"> | |||
ssh -p 2222 username(of local machine)@localhost | |||
</source> | |||
Note: port 2222 is an arbitrary number. We could have used any other available port. | Note: port 2222 is an arbitrary number. We could have used any other available port. | ||
| Line 27: | Line 33: | ||
Since HTTP traffic runs on port 80, instead of creating a tunnel attaching the ssh standart traffic port (22), '''we attach our chosen port .ie 12345 to port 80''' | Since HTTP traffic runs on port 80, instead of creating a tunnel attaching the ssh standart traffic port (22), '''we attach our chosen port .ie 12345 to port 80''' | ||
<source lang="bash"> | |||
ssh -N -T -R 12345:localhost:80 username@pzwart1.wdka.hro.nl | |||
</source> | |||
And follow the steps below: | And follow the steps below: | ||
Revision as of 08:17, 23 October 2017
To access a local machine, behind a firewall, without a public IP, we can use a reserve ssh tunnel - a poor man's VPN.
The steps are the following:
From the machine you want to access (local machine), create an ssh tunnel to a publicly accessible server (remote machine), like pzwart1:
ssh -N -T -R 2222:localhost:22 username@pzwart1.wdka.hro.nl
This command establish a tunnel with a -R remote entry point between the local machine and the remote machine .
This will allow, as we'll see later, that anything attached to port 2222 on the server, to reach "localhost port 22", The other options are:
- -f send ssh to background
- -N saves resources, by specifiying you don't actually want to run any remote commands. If all you're creating is a tunnel, then including this option.
- -T disables the interactive shell.
To access the localhost, from any where, all you need to do is login to the remote, as you normally do:
ssh username@pzwart1.wdka.hro.nl
Once inside the remote, you simply login to its own localhost, but on port 2222, which will reach "localhost port 22", which is is our
ssh -p 2222 username(of local machine)@localhost
Note: port 2222 is an arbitrary number. We could have used any other available port.
Tunnel http traffic
The same strategy used above to tunnel SSH traffic, can be used to tunnel HTTP traffic.
Since HTTP traffic runs on port 80, instead of creating a tunnel attaching the ssh standart traffic port (22), we attach our chosen port .ie 12345 to port 80
ssh -N -T -R 12345:localhost:80 username@pzwart1.wdka.hro.nl
And follow the steps below:
Here is the situation, you want to hide your IP behind a proxy, you need to access a resource that is blocking your IP but not the one of your proxy, etc.
You can do all that if you have an ssh account on another machine, using your ssh connection as an HTTP proxy (SOCKS type) is very easy.
- Open a connection to the server/machine you want to tunnel your traffic through:
ssh -D 12345 user@superserver
This will open a normal ssh session to superserver and create a SOCKS proxy on your local machine on port 12345.
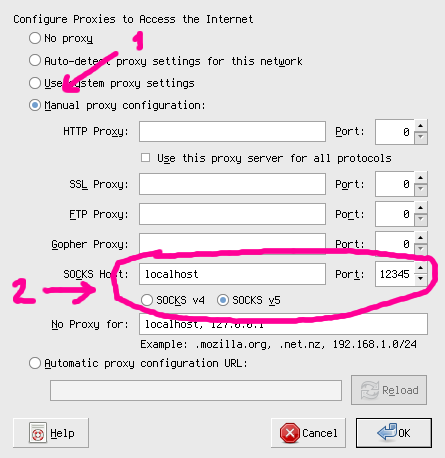
- Go to your browser's networking preferences and select SOCKS as proxy pointing to your localhost on port 12345. For example on firefox:
Notes
- You can just open a tunnel in the background without requesting a shell session:
ssh -fND 12345 user@superserver
- While you will be able to hide your real IP from the other servers you are connecting to, your IP and your actions can be easily traced back to your account on the server you're sshing in.