User:Andre Castro/2/thesis/formula: Difference between revisions
Andre Castro (talk | contribs) (Created page with "In this section I will use Vladimír Propp formalist analyzes of Russian fairy tales as models that when applied to spam email may provide a more insightful view over spam for...") |
Andre Castro (talk | contribs) No edit summary |
||
| (5 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
In this section I will use Vladimír Propp formalist | In this section I will use Vladimír Propp formalist study of the Russian fairy tales.Taking Propp's approach to the analysis of spam email messages may provide a more insightful view over spam formal characteristics. I will try to clarify if in spam, like in Russian folktales, their repetitive and predictable nature is counterbalanced by a picturesque and multiform manifestation of the stories. I would like to carry the discussion, by looking a repetition in wider are, trying to understand why is reoccurring and predictable narratives so present in popular culture, and why do we take pleasure in consuming those narratives? | ||
+ language of trust | |||
==Propp's ''Morphology of the Folktale''== | ==Propp's ''Morphology of the Folktale''== | ||
In 1928 Vladimír Propp (1928) proposed a formal analyses of Russian fairy tales. | In 1928 Vladimír Propp (1928) proposed a formal analyses of Russian fairy tales. Propp intended to establish a morphology of Russian folktales, a sort of list of ingredients and the sequence in which they enter the elaboration a Russian tale. In order to draw a morphology Propp studied the tales by focusing on the ''"the functions of its dramatis personae"''(Propp 1929 p.7). In other words, the study focuses on the ''what'' action is performed, and not on ''who'' performs it or ''how'' is performed, as "characters of a tale, however varied they may be, often perform the same action. The actual means of the realization of functions can vary, and as such, it is a variable... But the function, as such, is a constant" (ibid p. 8). A function is a slot belonging to an action, that will be filled both by the way its undertaken and the character who undertakes it. The function forms a constant and stable unit, while the latter constitute its variables. "''Function is understood as an act of the character, defined from the point of view of its significance for the course of the action''"(ibid p. 8). Let's take as an example the function 'lack'. Its summary tell us that "a member of the family lacks or desires something". And its subcategories states that several acts can perform that function, according to the object of lacking: the bride, a magical agent, or a wondrous object. | ||
It should be also noted that the acts performed within each function are interdependent, as in the function ''interdiction violated'', the subsequent violation will derive from the interdiction. | |||
Such system of fixed and finite elements, combined with interchangeable and numerous characters give the tale its "multiformity, picturesqueness, and color, and on the other hand, its no less striking uniformity, its repetition... The sequence of elements ... is strictly ''uniform''. Freedom within this sequence if restricted by very narrow limits which can exactly formulated" (Propp 1926, p.8). And even when certain function are excluded from a tale, the sequence remains unaltered. | Such system of fixed and finite elements, combined with interchangeable and numerous characters give the tale its "multiformity, picturesqueness, and color, and on the other hand, its no less striking uniformity, its repetition... The sequence of elements ... is strictly ''uniform''. Freedom within this sequence if restricted by very narrow limits which can exactly formulated" (Propp 1926, p.8). And even when certain function are excluded from a tale, the sequence remains unaltered. | ||
| Line 31: | Line 17: | ||
==dissecting spam== | |||
== | Adopting Propp's formal analysis I will dissect a number of 419s Fraud emails. I will do this simply by isolating its constituting plot events or functions into blocks that seem to be present in each of the emails. The emails and their functions can be seen at [[User: Andre_Castro/2/thesis/emails-functions | Email Functions ]] . | ||
Adopting Propp's formal analysis I will dissect a number 419s Fraud emails | |||
Note: Throughout the functions description I will use the term ''writer''. In this context ''writer'' refers not to the real author of the email, but to the fictional character, the persona, who is supposedly writes the email, and around whom the narrative revolves. | |||
[[Image:functions-graph.svg|right]] | |||
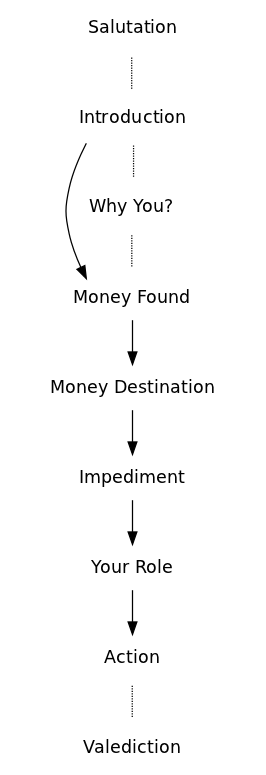
Nine | Nine functions have been identified, which follow, apart from a few exceptions, the given sequence: | ||
''Salutation'': The | ''Salutation'': The writer begins by saluting the reader. Often only with a plain "hi", others times the writer might already try to establish a bound with the reader using a more intimate approach "Hello Dearest One" writes Alima Kipkalya. | ||
''Why you?'': This function, while not central to the plot, tries to justify is the reader receiving such email. Often the | ''Why you?'': This function, while not central to the plot, tries to justify why is the reader receiving such email. Often the writer refers to her desperate situation, to which the reader can be a way out. This function often appears after the introduction. | ||
''Introduction'': The | ''Introduction'': The writer introduces herself. This is a pivotal moment for the narrative, since who the writer happens to be will dictated how the following functions are enacted. Possible characters found so far featuring the role of the writer were a banker, a family member of a state's person, a soldier, a rich but ill widow. | ||
''Money Origin'': The reader is told about the sum of money that took the | ''Money Origin'': The reader is told about the sum of money that took the writer to contact her. The money origin will depend on who is writing the email. The banker comes across money from a deceased client; the relative to the state's person inherits his fortune; the soldier finds money during an armed conflict; the terminally ill woman inherits her deceased husband fortune. | ||
''Money Destination'': The | ''Money Destination'': The writer describes the destination she wants to give to the money. This function is also dependent with who the writer is, if it happens to be an ill woman she will want to give the money to charity, the soldier on the other hands wants to keep it for himself. | ||
''Impediment'': | ''Impediment'': An impediment doesn't allow the money to remain with the writer and she informs the reader as why she isn't able to keep the money. Consequently she needs the reader's cooperation. Like with the ''Money Destination'' the impediment is not always clearly stated. Yet, it continues to be dependent on the who the writer is (''Introduction''). In the particular case of the banker Peter Hayman, it is hard to tell why can't he keep the funds from the deceased client; the daughter cannot checkout the money from the bank until she finds a husband or trustee, the soldier cannot keep the money as it is illegal, the widow is on the verge of death. | ||
| Line 68: | Line 53: | ||
''Action'' The receiver is urged to confirm her interest in the proposal by replying to the email and often by proving information on herself. She might be given instruction as what to how to act upon the | ''Action'' The receiver is urged to confirm her interest in the proposal by replying to the email and often by proving information on herself. She might be given instruction as what to how to act upon the writer's instruction. | ||
''Valediction'' concludes the email. It must be in accordance to whom the writer happens to be. The banker simply writes "Yours Faithfully", followed by his bank contact; the soldier with "Yours in Service"; and the devoted christian widow with "May the Grace of our Lord Jesus Christ,the love of God,and the fellowship of the Holy Spirit be with you and your family." | |||
Like in Propp's ''morphology'', functions essentially follow the same sequence throughout the studied emails. Yet it is common for these plots to employ a smaller amount of functions than the entire array of identified ones, as is the case of the email number one (from Peter Hayman). Functions also seem to be interrelated, since the way in which a function is instantiated will have repercussions on to how the following functions are concretized. Yet, the discrepancy between the thirty one functions identified by Propp and the meager nine identified in 419 fraud emails gives us an idea of the discrepancies between these two objects of study. | |||
Janet Murray describes Vladímir Propp's ''Morphology of the Folktale'', as "a recipe for Russian folktale...[which] makes clear that the formulaic underpinning makes folktales more intricate; it allows storytellers to weave together multiple different story sequences without becoming confused" (Murray 1998 p.196). In Murray's opinion the formula Propp describes is far more complex than the ones employed in the construction of computer games. "Games ... are usually constructed with only shallow detours off the main spine of the plot...Games that do provide narrative variety often do so through a simple substitution system...But games do not allow substitution of thematic plot elements ... the way fairy tales do. Games are limited to very rigid plotlines because they do not have an abstract representation of the story structure that would allow them to distinguish between a particular instantiation and a generic morpheme" (ibid, p.198). | |||
If we take a second look at spam, in the light of Murray's criticism of computer game's narrative formulas, we might be inclined to see the 419s' structural representation as closer those of games, rather than the ramified and interlaced structure of Russian fairy tales. Although the writer changes, and with it so does the mood of the email (the mode of address, the argumentation, etc), there is not much of a change in plot, it remains essentially the same. One very obvious reason for such repetition lays the funneling of the narrative into convincing the reader to give away personal data and money, just like most computer games drive the player into getting towards the end or outrunning the opponent. In folktales, on the other hand, we might see a variety of ''programs'', from building a national identify - the Grimm brothers -, to inciting a moral behavior, to the upsetting of conventions. Whiles in spam the plot remains essential the same: I have money, you need to help me to keep it, if you help you will be rewarded. This unchangeable construction fails to surprise us, yet we keep on reading them and often finding ourselves amused by those predictable stories. | |||
Yet spam is popular! I suspect that in part, spam's popularity stems from its capacity to meet our expectations. It comforts us to know that a story will end and as we expect. An American soldier who send us an email asking for help, will behave as expected, as a prince in a fairy tale. If the soldier, decides to hand-over the money found to the Afghans, it would as catastrophic as the prince, after seizing power over his kingdom becomesa brutal dictator. In both situations our certainties and believes will be shaken up and brought into question, which is something spammers want do not want to call upon, as they require the blind trust from readers, so that the scam might be carried out. | |||
Jena Burrel, based on her field-work with the population of young Ghana's spammers, reports that when posing as Africans, spammers would integrate into their character the "Western archetype of the African other". Burrel describes them as ''self-aware mimics'', specialized in representing their online persona based on Western archetypes of the African Other. In this way they were trying to meet the expectations of the foreign gaze that "expected an asymmetry, expected and responded to them as needy, but not as potential partners. It expected medical bills, not IT schools". (Calibre: 187.4-192.0 / 571) | |||
Consequently spammers responded by providing the expected image, such as the poor orphan, the attractive woman, the corrupt politician, or the Christian pastor | |||
---- | |||
And fairy tales have been known to play a role in affirming national identities. A safe world, made of certainties, and expected endings is necessary to build on trust and investment. | |||
* the use of folktales to build national identities | |||
* Use of stereotypes by spammers | |||
* the language of trust in advertisement | |||
* moral function of folktales | |||
<pre> | |||
Yet there is a richness to spam, that deserves not to be overlooked. At the onset the scenarios and characters portrayed are very rich. Could it be that spam messages could server as an initial scenario, prone to be appropriated and given an unexpected development, similarly to the appropriation of computer games by artists? | |||
the plot | [PROJECT IDEA: Copy the first part of spam mail and write them into a postcard, living the remaining plot to be filled by the recipient. Once complete send the mail back to me. ] | ||
These fixed structure fails to surprise us. Simple variations on the same formula could be something like: I have been scammed, as I and poor i cannot afford to prosecute the scammer, therefore I need your monetary help, if I win you'll get a reward. | These fixed structure fails to surprise us. Simple variations on the same formula could be something like: I have been scammed, as I and poor i cannot afford to prosecute the scammer, therefore I need your monetary help, if I win you'll get a reward. | ||
| Line 107: | Line 102: | ||
[ISN'T SPAMMER ALREADY USING THIS TYPE OF PLOTS ??] | [ISN'T SPAMMER ALREADY USING THIS TYPE OF PLOTS ??] | ||
"By generating multiple stories that look very different on the surface but that derive from the same underlying moral physics, an author-directed cyberdrama could offer and encyclopedic fictional world whose possibilities would only be exhausted at the point of the interactor's saturation with the core conflict" (p.209). | "By generating multiple stories that look very different on the surface but that derive from the same underlying moral physics, an author-directed cyberdrama could offer and encyclopedic fictional world whose possibilities would only be exhausted at the point of the interactor's saturation with the core conflict" (p.209). | ||
</pre> | |||
| Line 128: | Line 121: | ||
* re-iterate what the readers know; they live on clichés of Africa and Africans; | |||
''Is repetition and predictability interesting for readers? Do they prefer it to unknown and unpredictable plots'' | ''Is repetition and predictability interesting for readers? Do they prefer it to unknown and unpredictable plots'' | ||
| Line 178: | Line 175: | ||
* Propp, Vladímir. 1929. 'Morphology of the Folk Tale' The American Folklore Society and Indiana University. | * Propp, Vladímir. 1929. 'Morphology of the Folk Tale' The American Folklore Society and Indiana University. | ||
* Burrell, Jena. 2012. 'Invisible Users: Youth in the Internet Cafés of Urban Ghana'. MIT Press. Cambridge / London. | |||
Latest revision as of 11:05, 14 February 2013
In this section I will use Vladimír Propp formalist study of the Russian fairy tales.Taking Propp's approach to the analysis of spam email messages may provide a more insightful view over spam formal characteristics. I will try to clarify if in spam, like in Russian folktales, their repetitive and predictable nature is counterbalanced by a picturesque and multiform manifestation of the stories. I would like to carry the discussion, by looking a repetition in wider are, trying to understand why is reoccurring and predictable narratives so present in popular culture, and why do we take pleasure in consuming those narratives?
+ language of trust
Propp's Morphology of the Folktale
In 1928 Vladimír Propp (1928) proposed a formal analyses of Russian fairy tales. Propp intended to establish a morphology of Russian folktales, a sort of list of ingredients and the sequence in which they enter the elaboration a Russian tale. In order to draw a morphology Propp studied the tales by focusing on the "the functions of its dramatis personae"(Propp 1929 p.7). In other words, the study focuses on the what action is performed, and not on who performs it or how is performed, as "characters of a tale, however varied they may be, often perform the same action. The actual means of the realization of functions can vary, and as such, it is a variable... But the function, as such, is a constant" (ibid p. 8). A function is a slot belonging to an action, that will be filled both by the way its undertaken and the character who undertakes it. The function forms a constant and stable unit, while the latter constitute its variables. "Function is understood as an act of the character, defined from the point of view of its significance for the course of the action"(ibid p. 8). Let's take as an example the function 'lack'. Its summary tell us that "a member of the family lacks or desires something". And its subcategories states that several acts can perform that function, according to the object of lacking: the bride, a magical agent, or a wondrous object.
It should be also noted that the acts performed within each function are interdependent, as in the function interdiction violated, the subsequent violation will derive from the interdiction.
Such system of fixed and finite elements, combined with interchangeable and numerous characters give the tale its "multiformity, picturesqueness, and color, and on the other hand, its no less striking uniformity, its repetition... The sequence of elements ... is strictly uniform. Freedom within this sequence if restricted by very narrow limits which can exactly formulated" (Propp 1926, p.8). And even when certain function are excluded from a tale, the sequence remains unaltered.
dissecting spam
Adopting Propp's formal analysis I will dissect a number of 419s Fraud emails. I will do this simply by isolating its constituting plot events or functions into blocks that seem to be present in each of the emails. The emails and their functions can be seen at Email Functions .
Note: Throughout the functions description I will use the term writer. In this context writer refers not to the real author of the email, but to the fictional character, the persona, who is supposedly writes the email, and around whom the narrative revolves.
Nine functions have been identified, which follow, apart from a few exceptions, the given sequence:
Salutation: The writer begins by saluting the reader. Often only with a plain "hi", others times the writer might already try to establish a bound with the reader using a more intimate approach "Hello Dearest One" writes Alima Kipkalya.
Why you?: This function, while not central to the plot, tries to justify why is the reader receiving such email. Often the writer refers to her desperate situation, to which the reader can be a way out. This function often appears after the introduction.
Introduction: The writer introduces herself. This is a pivotal moment for the narrative, since who the writer happens to be will dictated how the following functions are enacted. Possible characters found so far featuring the role of the writer were a banker, a family member of a state's person, a soldier, a rich but ill widow.
Money Origin: The reader is told about the sum of money that took the writer to contact her. The money origin will depend on who is writing the email. The banker comes across money from a deceased client; the relative to the state's person inherits his fortune; the soldier finds money during an armed conflict; the terminally ill woman inherits her deceased husband fortune.
Money Destination: The writer describes the destination she wants to give to the money. This function is also dependent with who the writer is, if it happens to be an ill woman she will want to give the money to charity, the soldier on the other hands wants to keep it for himself.
Impediment: An impediment doesn't allow the money to remain with the writer and she informs the reader as why she isn't able to keep the money. Consequently she needs the reader's cooperation. Like with the Money Destination the impediment is not always clearly stated. Yet, it continues to be dependent on the who the writer is (Introduction). In the particular case of the banker Peter Hayman, it is hard to tell why can't he keep the funds from the deceased client; the daughter cannot checkout the money from the bank until she finds a husband or trustee, the soldier cannot keep the money as it is illegal, the widow is on the verge of death.
Your role: The reader is informed as what her role will be within the portrayed scenario. The reader also learns about her reward for helping out: "It is my intention to compensate you with 30% of the total money for your services", states Alima Kipkalya Kones.
Action The receiver is urged to confirm her interest in the proposal by replying to the email and often by proving information on herself. She might be given instruction as what to how to act upon the writer's instruction.
Valediction concludes the email. It must be in accordance to whom the writer happens to be. The banker simply writes "Yours Faithfully", followed by his bank contact; the soldier with "Yours in Service"; and the devoted christian widow with "May the Grace of our Lord Jesus Christ,the love of God,and the fellowship of the Holy Spirit be with you and your family."
Like in Propp's morphology, functions essentially follow the same sequence throughout the studied emails. Yet it is common for these plots to employ a smaller amount of functions than the entire array of identified ones, as is the case of the email number one (from Peter Hayman). Functions also seem to be interrelated, since the way in which a function is instantiated will have repercussions on to how the following functions are concretized. Yet, the discrepancy between the thirty one functions identified by Propp and the meager nine identified in 419 fraud emails gives us an idea of the discrepancies between these two objects of study.
Janet Murray describes Vladímir Propp's Morphology of the Folktale, as "a recipe for Russian folktale...[which] makes clear that the formulaic underpinning makes folktales more intricate; it allows storytellers to weave together multiple different story sequences without becoming confused" (Murray 1998 p.196). In Murray's opinion the formula Propp describes is far more complex than the ones employed in the construction of computer games. "Games ... are usually constructed with only shallow detours off the main spine of the plot...Games that do provide narrative variety often do so through a simple substitution system...But games do not allow substitution of thematic plot elements ... the way fairy tales do. Games are limited to very rigid plotlines because they do not have an abstract representation of the story structure that would allow them to distinguish between a particular instantiation and a generic morpheme" (ibid, p.198).
If we take a second look at spam, in the light of Murray's criticism of computer game's narrative formulas, we might be inclined to see the 419s' structural representation as closer those of games, rather than the ramified and interlaced structure of Russian fairy tales. Although the writer changes, and with it so does the mood of the email (the mode of address, the argumentation, etc), there is not much of a change in plot, it remains essentially the same. One very obvious reason for such repetition lays the funneling of the narrative into convincing the reader to give away personal data and money, just like most computer games drive the player into getting towards the end or outrunning the opponent. In folktales, on the other hand, we might see a variety of programs, from building a national identify - the Grimm brothers -, to inciting a moral behavior, to the upsetting of conventions. Whiles in spam the plot remains essential the same: I have money, you need to help me to keep it, if you help you will be rewarded. This unchangeable construction fails to surprise us, yet we keep on reading them and often finding ourselves amused by those predictable stories.
Yet spam is popular! I suspect that in part, spam's popularity stems from its capacity to meet our expectations. It comforts us to know that a story will end and as we expect. An American soldier who send us an email asking for help, will behave as expected, as a prince in a fairy tale. If the soldier, decides to hand-over the money found to the Afghans, it would as catastrophic as the prince, after seizing power over his kingdom becomesa brutal dictator. In both situations our certainties and believes will be shaken up and brought into question, which is something spammers want do not want to call upon, as they require the blind trust from readers, so that the scam might be carried out.
Jena Burrel, based on her field-work with the population of young Ghana's spammers, reports that when posing as Africans, spammers would integrate into their character the "Western archetype of the African other". Burrel describes them as self-aware mimics, specialized in representing their online persona based on Western archetypes of the African Other. In this way they were trying to meet the expectations of the foreign gaze that "expected an asymmetry, expected and responded to them as needy, but not as potential partners. It expected medical bills, not IT schools". (Calibre: 187.4-192.0 / 571)
Consequently spammers responded by providing the expected image, such as the poor orphan, the attractive woman, the corrupt politician, or the Christian pastor
And fairy tales have been known to play a role in affirming national identities. A safe world, made of certainties, and expected endings is necessary to build on trust and investment.
- the use of folktales to build national identities
- Use of stereotypes by spammers
- the language of trust in advertisement
- moral function of folktales
Yet there is a richness to spam, that deserves not to be overlooked. At the onset the scenarios and characters portrayed are very rich. Could it be that spam messages could server as an initial scenario, prone to be appropriated and given an unexpected development, similarly to the appropriation of computer games by artists? [PROJECT IDEA: Copy the first part of spam mail and write them into a postcard, living the remaining plot to be filled by the recipient. Once complete send the mail back to me. ] These fixed structure fails to surprise us. Simple variations on the same formula could be something like: I have been scammed, as I and poor i cannot afford to prosecute the scammer, therefore I need your monetary help, if I win you'll get a reward. I want to invest in a profitable business, I lack the funds for it, if you become a co-investor you will receive part of the profit [ISN'T SPAMMER ALREADY USING THIS TYPE OF PLOTS ??] "By generating multiple stories that look very different on the surface but that derive from the same underlying moral physics, an author-directed cyberdrama could offer and encyclopedic fictional world whose possibilities would only be exhausted at the point of the interactor's saturation with the core conflict" (p.209).
I will follow analysis with a discussing what forms of agencies does such a two-fold (repetitive and multiform) quality equip spam's 419s with.
[WHAT 2-FOLD NATURE DO TO SPAM]
repetition and predictability
WHAT DOES THE REPETITION PROVIDE THE TALE OR READERS? Its uniform and repetitive nature allows the audience to know what will be the next action, what will happen to he hero at a give moment, how will he react, etc. [ Why is the uniformity important ??]
- re-iterate what the readers know; they live on clichés of Africa and Africans;
Is repetition and predictability interesting for readers? Do they prefer it to unknown and unpredictable plots
Yet, yes the repetition of the same pattern and the predictability of the plot development playing for or against the spammers? Is it
Repetition and predictability is not something that human audience abject. Popular cultural is filled with examples that thrive on the repetition and foreseeable sequence of events. Clear examples are for instance the James Bond movies, or Italian Commedia dell'arte. Our expectations might be met when Miss Alima Kipkalya Kones asks us to help checkout her deceased father fortune. (The stories ends as we predicted and we fill good about it. Perhaps we don't want to be that challenged by the narrative. We can even speculate on that being the reason that multiform and interactive narrative hasn't yet been accomplished and met with wide audience's interest)
[COULD THE OLIPIO SUBSTITUTION GAMES BE A WAY OUT??]
the substitution of a word for another, could change quite substantially the narrative.
http://web.archive.org/web/20060508084853/http://www.oulipocompendium.com/html/excerpt_frame.html
ideas to develop
- email as space of attention
- email as form of communication, not a medium commonly used to narrate stories.
- Murray - suspension of disbelief
writing character - the central variable. It will dictacte the rest of the narrative:
- how she came across the money
- the impediment to get hold of money
- writing character decorates the storie with the punctuation that will correspond to the expectation towards character.
- exagerated, forming almost a caricature of that character
- commedia dell'arte
bibliography
- Murray, Jannet. 1998. 'Hamlet on the Holodeck: The Future of Narrative in Cyberspace'. MIT Press. Cambridge / London.
- Propp, Vladímir. 1929. 'Morphology of the Folk Tale' The American Folklore Society and Indiana University.
- Burrell, Jena. 2012. 'Invisible Users: Youth in the Internet Cafés of Urban Ghana'. MIT Press. Cambridge / London.