User:Michaela/Worklog: Difference between revisions
No edit summary |
|||
| (One intermediate revision by the same user not shown) | |||
| Line 44: | Line 44: | ||
'''Data collection''' consists of rich content of personal data/ img files, videos files, audio files, code or text logs, which are hard to read and trash (or unrecoverable files, parasite files etc.)<br> | '''Data collection''' consists of rich content of personal data/ img files, videos files, audio files, code or text logs, which are hard to read and trash (or unrecoverable files, parasite files etc.)<br> | ||
How this can be brought back to the system of data erase?<br> | |||
'''Data presentation or possible outcome:''' <br> | '''Data presentation or possible outcome:''' <br> | ||
</div> | </div> | ||
==Used Tools== | ==Used Tools== | ||
'''PROCESS''' <br> | '''PROCESS''' <br> | ||
<br> | |||
The process of data retrial could be seen --> | The process of data retrial could be seen --> | ||
[http://pzwart3.wdka.hro.nl/~mlakova/data_erasure/captcha_photorec.mp4 '''HERE''']<br> | [http://pzwart3.wdka.hro.nl/~mlakova/data_erasure/captcha_photorec.mp4 '''HERE''']<br> | ||
The sound of the Hard drive could be listen --> | The sound of the Hard drive could be listen --> | ||
[http://pzwart3.wdka.hro.nl/~mlakova/data_erasure/hard_sound.wav '''HERE'''] | [http://pzwart3.wdka.hro.nl/~mlakova/data_erasure/hard_sound.wav '''HERE''']<br> | ||
<br> | |||
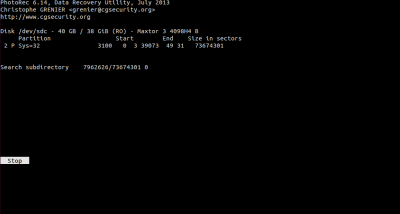
[http://www.cgsecurity.org/ '''TestDisk'''] undeletes files from FAT, NTFS, exFAT and ext2 filesystem.<br> | [http://www.cgsecurity.org/ '''TestDisk'''] undeletes files from FAT, NTFS, exFAT and ext2 filesystem.<br> | ||
[http://www.cgsecurity.org/wiki/PhotoRec '''PhotoRec'''] is an an open-source tool for data recover lost files, including video, documents and archives from hard disks. | [http://www.cgsecurity.org/wiki/PhotoRec '''PhotoRec'''] is an an open-source tool for data recover lost files, including video, documents and archives from hard disks. | ||
==Performative code == | ==Performative code == | ||
Latest revision as of 15:42, 3 December 2013
Description
In this project I am collecting discarded hard drives and retrieving data traces out of them in order to examine abandoned data and leftover traces. A collection of ten hard drives was purchased as a commodity on Marktplaats. The hard drive rather ubiquitous objects serve as an ultimate storage of data, container of past and present, which could be also invade, investigate and dissected.
The traces of information are exponential they contain various sources ..they travel, scattered being trade or serve as a found footage for artistic intervention.
This experiment is trigger by the idea of how the data trace is permanent,it could not be not destroyed or erased completely. It has been encapsulated within time, the code and the medium itself.
How the act of disclosure is already a critic?
I am interested in the ethical aspect or who has the right to retrieve someone's data?
Or who owns the ownership of this data?
In my research I am looking at the general themes of digital waste, e-waste... data erasure – the physically destruction of data as the ultimate mode of complete erase.
Discoveries
The material I found so far is rich source of various items: personal images, videos ( family portraits, old amateur videos - dating from the late 70s - 80s, assigned to various trips). Some of these files are usually corrupted movie files failing to succeed to the recovery process. screenshots HERE
- The factory set is a 23 min long video documentation of factory for pineapples in Ghana.
The camera follows the production line of workers assembling pineapples, scene by scene every detail of the process. The moving images are rich by their source of origin, revealing highly graphical, dense scene of workers in factory motionless in their every day basics, just performing repetitive actions. The images serve as a data trails, conveying the trace of the failure of the recovery process, signed for being "broken" or interrupted. Sometimes the freeze of the frame creates conscious break from the meditation, but also suggest that the footage has been manipulated.
--> screenshots of the footage could be found HERE
Meta data missing
In this case there is no actual meta data...only evidences of time and space, found in the real footage or rather assigned from the quality of the footage itself. In this concept the tag is missing. The viewer could add an extra layer of the unknown time and space of when and where they took place.
For instance in the video of the factory workers there is an evidence of the place or a distinguish sign of the company name: Tongu fruits GHANA LTD, which could serve as tracking trace or geotag.
Methodology for data recover
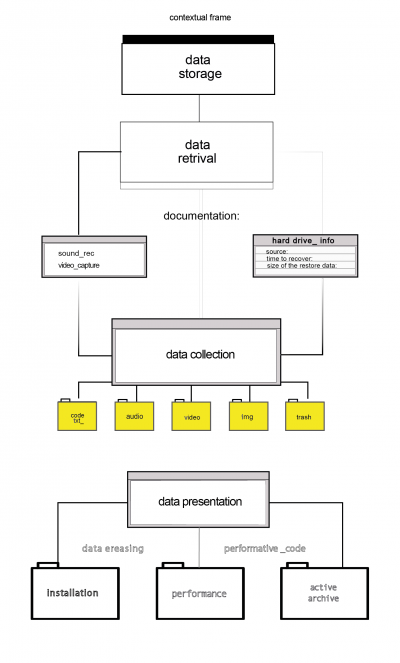
I built simple methodology of data recovery. The data storage is the approached collection of ten hard drives following by the information about the hard drive : the source of origin ()
The documentation or the process of recovery consists of the video capture of the used software and the sound from a spinning hard drive disk (unable to be booted). In order to organize this accidentally found archive I simply described the size/ model of each hard drive, the process of the remain time and amount of the restored data.
Data collection consists of rich content of personal data/ img files, videos files, audio files, code or text logs, which are hard to read and trash (or unrecoverable files, parasite files etc.)
How this can be brought back to the system of data erase?
Data presentation or possible outcome:
Used Tools
PROCESS
The process of data retrial could be seen -->
HERE
The sound of the Hard drive could be listen -->
HERE
TestDisk undeletes files from FAT, NTFS, exFAT and ext2 filesystem.
PhotoRec is an an open-source tool for data recover lost files, including video, documents and archives from hard disks.