User:Andre Castro/2.1/semniar-2012-10-10-summary: Difference between revisions
Andre Castro (talk | contribs) |
Andre Castro (talk | contribs) No edit summary |
||
| (12 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
=Project Proposal Draft= | =Project Proposal Draft= | ||
Tentative title | ==Tentative title== | ||
'''RE:''' | |||
==Short Description== | ==Short Description== | ||
For many of us our relation with spam emails consists in moving them from the inbox to the junk-mail folder | For many of us our relation with spam emails consists in moving them from the inbox to the junk-mail folder of our email accounts. Yet, if we take a close look at some of the unsolicited emails we receive we might find them curious, and may even be amuse by them. We might even begin to see them as a literary creation, in which considerable amounts of inventiveness, and awareness to the current global situation, as well as knowledge about society's soft-spots are explored in order to produce a persuasive message. Besides, curious glitches abound such as the heavy use of stereotypes, Google-translate misinterpretations, typos, word obfuscations, and recurring text fragments. Being it such an idiosyncratic and rich area of text production I believe it deserves to be embraced as a literary genre. Being it so, I am interested in exploring it as a literary device, as a template for writing and communication. | ||
Being it such an idiosyncratic and rich area of text production I believe it | |||
==Methodology== | |||
As already mentioned, for various and legitimate reasons, we don't pay much attention to spam email messages. Would we then start to read and respond to them, if rather than trying to persuades us to join some money winning (or loosing) scheme, spam emails would try to seduce us to take part in a shared writing process with someone distant and unknown? | |||
I would like to provide a positive answer to this question. My strategy for attempting to do so will be based upon the appropriation of spam as a literary device. In order to do it, I conceived a system summed up in the following diagram. | |||
[[File:Diagram-Pingme.png|left]] | |||
'''1)''' To initiate the process I will take on the role of a spammer, who sends unsolicited emails (to be more precise, just one email) to a large number of addresses of unknown individuals. This first email will take on the same structure as most spam messages, comprising exposition of the great opportunity one has just been given, followed by the argumentation to why one should take part in it. | |||
'''2)''' If a receiver answers, her message will be replied from my side through a bot, who will analyze the received message at different levels (e.g. letter occurrence, word occurrence, keywords, and phrases) and produce a reply that will try to respond to it, but also push it into other directions, as my aim is to tell and be told short stories through these these text exchanges. | |||
The email exchange between bot and human receiver will go on for a few times, after which it will be interrupted and followed by stage 3. | |||
'''3)''' At this point the bot will step back from its reader-writer function, and become a proxy, that will forward the messages between two human receivers, who happen be in a similar stage of writing process. | |||
' | The two, now connected, human receivers won't be notified of this change. It will be up to them how to continue the dialogue and discover the one at the other end. | ||
The bot will server as an agent who mediates connections between humans, both between me and the receivers, and between two receivers. | |||
' | Note: This is one possible way of integrating the referred elements, and I want to try it fully, so that I can see what results it produces. However it doesn't have to be the definitive way of doing it. Perhaps at later stage I will rearrange the same elements differently, and bring in new elements and methods. | ||
| Line 44: | Line 44: | ||
===Outcome=== | |||
As a first raw outcome I want to store all the communication history between myself (the bot) and the receivers; if possible I would also like to keep track of the receiver to receiver exchange. Yet, at this moment I cannot decide upon a final outcome for the project. Some possibilities are a radio-play, a book, or a map of these exchanges (taking time as one of its dimensions). | |||
===A first test email=== | ===A first test email=== | ||
As a first test I | As a first test I decided to email some random addresses from my address-book and see if any replies would ping back. Here is the email sent and its replies: | ||
Here is email sent and | |||
<source lang="email"> | <source lang="email"> | ||
| Line 135: | Line 134: | ||
</source> | </source> | ||
===Other prototypes=== | |||
In order to engage with email spam I have made few prototypes, so that I'd gain more insight into it. | |||
They consisted in: | |||
* '''Archive of Spam email''' - [[soon to be put online]] | |||
* '''Email exchanges with Mr. Wang, a banker in China who asked for my help in order to release a large sum of money frozen in his bank''' | |||
==General Work Methodology== | ==General Work Methodology== | ||
| Line 141: | Line 151: | ||
A stage of experimentation and research generally follows. At this point I try to broaden my question, find possible angles to approach it, find other approaches to similar problems, engage with my subject and experiment. The | A stage of experimentation and research generally follows. At this point I try to broaden my question, find possible angles to approach it, find other approaches to similar problems, engage with my subject and experiment. The engagement with the subject seems crucial, it is a step towards the object of research, into trying to look at it closely, and to establish a dialog with it. This happen more clearly in Data Factory where I tried to convince direct-marking companies' employees into talking with me and answer my questions about direct-marking and users' privacy. | ||
The following stage is one of concretization of the elected approach, bringing it from its experimental stage, through various prototypes to its final from. It is at this point when most decisions are made, such as what to include, in what context should it exist, how it will function, and what will be its material presence. | |||
The resulting object is rarely, a solution for the problem which initiated the work process. Rather than providing an answer it will be an imaginative solution that ought pose more questions, show the problem under another, perhaps unexpected, perspective. Hopefully such approach will challenge the value of the object in question, and allow it to reveal itself under another form. | |||
==Description of my previous works in the past year== | |||
To begin with I started by [http://pzwart3.wdka.hro.nl/wiki/User:Andre_Castro/WritingResearch/essay01 writing on the performativity of code]. Departing from Katherine Hayle's notion of code performativity I went on looking at how does code perform. How does code, rather than being a descriptive tool, has the capacity to act, to change things in the real world, similarly to a performative speech-act, such as a judge stating: "I pronounce you guilty of the crime", and often with more direct and material effects. | |||
Simultaneously I developed and [http://pzwart3.wdka.hro.nl/~acastro/map/ online map of the streets of Rotterdam]. This map - a striped-down version of the original map of Rotterdam - only displayed the city street names against a black background, on the browser. By clicking on each street a request was made to the City of Rotterdam's Archive to provide information on that particular street's name origin. That information was then displayed alongside the map. What I seemed to be creating here was an interface to access city's archive through a different channel. By having the indexes of the archive - the street names - displayed on the screen I might see and ask for information on streets that I wouldn't normally be interested in. It opened up the possibility for a serendipitous navigation through the city history. | |||
[[File:Name-map-02.png|thumb|right]] | [[File:Name-map-02.png|thumb|right]] | ||
The same serendipitous exploration made its way to the next project, [Radio Liberté Egalité Beyoncé (RLEB)]. RLEB was an online radio-station with a schedule composed of audio content fetched form Internet Archive. One-hour long cycles presented the listener with ten-minutes chunks of various sound materials, picked at chance the archive, | The same serendipitous exploration made its way to the next project, [Radio Liberté Egalité Beyoncé (RLEB)]. RLEB was an online radio-station with a schedule composed of audio content fetched form Internet Archive. One-hour long cycles presented the listener with ten-minutes chunks of various sound materials, picked at chance from the archive, within a specific categories, such as french talk-shows, hiphop, poetry readings, ambient music, etc. The design of website where RLEG was hosted presented a drawing of radio, with which the listener had to interact in order to get the radio playing. | ||
[[File:Radio_LEB.png|thumb|right]] | [[File:Radio_LEB.png|thumb|right]] | ||
[http://pzwart3.wdka.hro.nl/wiki/User:Andre_Castro/research/1.2/essay-archive The essay] written alongside the RLEB began by tracing the archive's historical ties to power, functioning as a legitimator of power and knowledge. It mentioned the ideology which underlies any archive, even folkloric archive such as Youtube, an which can be best perceived through what is kept from entering the archive. Never-the-less important differences exist between a physical offline archive and a digital online one: the latter has the potential of a wider access, and also to let its item be taken by visitors, without risk of | [http://pzwart3.wdka.hro.nl/wiki/User:Andre_Castro/research/1.2/essay-archive The essay] written alongside the RLEB began by tracing the archive's historical ties to power, functioning as a legitimator of power and knowledge. It mentioned the ideology which underlies any archive, even folkloric archive such as Youtube, an which can be best perceived through what is kept from entering the archive. Never-the-less important differences exist between a physical offline archive and a digital online one: the latter has the potential of a wider access, and also to let its item be taken by visitors, without the risk of impoverishment. These differences result in an invitation for appropriation of the digital archive. When one of its items is taken and transformed, a new version of it appears, and a certain confusion emerges over its origin - which one is the original and which is fictitious? When remixed versions surface, they change the archive into a space of dialogue and emergence of discourses, rather than a site for safekeeping and knowledge legitimization. | ||
[http://andrecastro.info/data-factory/ Data Factory] looked at direct marking companies' acquisition of consumers data | [http://andrecastro.info/data-factory/ Data Factory] looked at direct marking companies' acquisition of consumers data. It consisted of a small archive of recordings of phone-calls made to such companies. During the calls I tried to sell them their business's main ingredient - consumer data - with the catch being that "consumer" in this context meant only myself. Through the reactions to this simple short-circuit the ideology behind such business model became more apparent. The calls were gathered on a website, with a certain corporate style, in which they could be listened to, in parallel with images illustrating or ridiculing what was being said. | ||
[[File:DataFactory-04.png|thumb|right]] | [[File:DataFactory-04.png|thumb|right]] | ||
[http://pzwart3.wdka.hro.nl/wiki/Andre_Castro/research/1.3/review_1 The essay The Work of Audiences] departed from Dallas Smythe's | [http://pzwart3.wdka.hro.nl/wiki/Andre_Castro/research/1.3/review_1 The essay The Work of Audiences] departed from Dallas Smythe's text ''On the Audience Commodity and its Work''. In Smythe's view, the audience job consists in creating demand for advertised goods. What advertisers buy when placing an advert on a magazine, TV-show of website is the audiences' attention and their capacity to buy what is being advertised. It happens that the labor of this immaterial work-force changed under the Web 2.0, as noted by Andrejevic. Audiences are no longer simply asked to generate demand for advertised goods, but also to put their creativity to work in producing many of the contents that surround those adverts. By doing so audiences also develop a community around their creations, and produce information about their behavior, which will be used in targeted advertisement directed at them. In exchange audiences receive a small amount of control over their creations, which are ultimately property of the company hosting them. Following this line of thought I asked whether there was a difference from the work of audiences on platform like Youtube to one like Wikipedia. The situation seems to be that although Wikipedia relies on audiences' free creative labor, they are given more control over their creations, and engage in discussions over the functioning of Wikipedia. Is this difference enough for the work of audiences to be classified as less exploitative than the one done for Youtube? | ||
Latest revision as of 15:30, 6 December 2012
Project Proposal Draft
Tentative title
RE:
Short Description
For many of us our relation with spam emails consists in moving them from the inbox to the junk-mail folder of our email accounts. Yet, if we take a close look at some of the unsolicited emails we receive we might find them curious, and may even be amuse by them. We might even begin to see them as a literary creation, in which considerable amounts of inventiveness, and awareness to the current global situation, as well as knowledge about society's soft-spots are explored in order to produce a persuasive message. Besides, curious glitches abound such as the heavy use of stereotypes, Google-translate misinterpretations, typos, word obfuscations, and recurring text fragments. Being it such an idiosyncratic and rich area of text production I believe it deserves to be embraced as a literary genre. Being it so, I am interested in exploring it as a literary device, as a template for writing and communication.
Methodology
As already mentioned, for various and legitimate reasons, we don't pay much attention to spam email messages. Would we then start to read and respond to them, if rather than trying to persuades us to join some money winning (or loosing) scheme, spam emails would try to seduce us to take part in a shared writing process with someone distant and unknown?
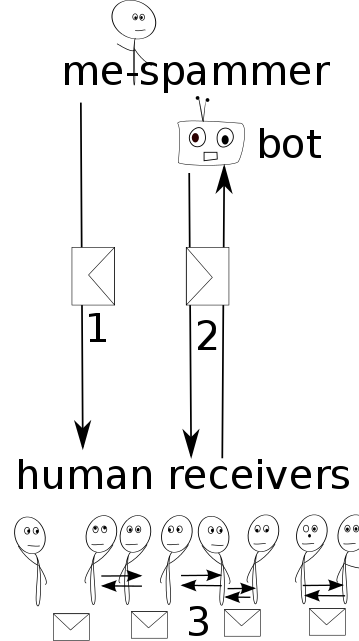
I would like to provide a positive answer to this question. My strategy for attempting to do so will be based upon the appropriation of spam as a literary device. In order to do it, I conceived a system summed up in the following diagram.
1) To initiate the process I will take on the role of a spammer, who sends unsolicited emails (to be more precise, just one email) to a large number of addresses of unknown individuals. This first email will take on the same structure as most spam messages, comprising exposition of the great opportunity one has just been given, followed by the argumentation to why one should take part in it.
2) If a receiver answers, her message will be replied from my side through a bot, who will analyze the received message at different levels (e.g. letter occurrence, word occurrence, keywords, and phrases) and produce a reply that will try to respond to it, but also push it into other directions, as my aim is to tell and be told short stories through these these text exchanges.
The email exchange between bot and human receiver will go on for a few times, after which it will be interrupted and followed by stage 3.
3) At this point the bot will step back from its reader-writer function, and become a proxy, that will forward the messages between two human receivers, who happen be in a similar stage of writing process.
The two, now connected, human receivers won't be notified of this change. It will be up to them how to continue the dialogue and discover the one at the other end.
The bot will server as an agent who mediates connections between humans, both between me and the receivers, and between two receivers.
Note: This is one possible way of integrating the referred elements, and I want to try it fully, so that I can see what results it produces. However it doesn't have to be the definitive way of doing it. Perhaps at later stage I will rearrange the same elements differently, and bring in new elements and methods.
Outcome
As a first raw outcome I want to store all the communication history between myself (the bot) and the receivers; if possible I would also like to keep track of the receiver to receiver exchange. Yet, at this moment I cannot decide upon a final outcome for the project. Some possibilities are a radio-play, a book, or a map of these exchanges (taking time as one of its dimensions).
A first test email
As a first test I decided to email some random addresses from my address-book and see if any replies would ping back. Here is the email sent and its replies:
From: . <.@gmail.com>
It looks like you're writing a letter.
I hope I am not making a mistake, but I think it would be a nice
experience to writing with you.
I must say my writing is all over the place, I can't just stand still.
You know that feeling?
verrrrr veeeerrr verrrr bossss verbose!
and sttutt ttt t eeeringgg stuttering on words??
........................................
........................................
...........................................
....................a....................
............a................a...........
........a.a...........a..............a....
.a................a............a........
OH! Probably I have just now manage to confuse you big time
Confusion can be a natural state /kənˈfjuːʒən/ as well as passivity
/pæsɪv/ and also procrastination /pɹəʊ̆ˌkɹæstɪˈneɪʃə̆n/
Write me some lines, I can only promise it doesn't get any better than this.
And these are the received replies
From: Konsul Gnadenwalze
01101000 01100001 01101000 01100001 00100000 01100111 01110010 01100101
01100001 01110100 00101100 00100000 01101101 01101111 01110010 01100101
00100000 01110000 01101100 01100101 01100001 01110011 01100101 00101110
00100000 00101101 00100000 01100100 01100101 01110010 00100000 01101011
01101111 01101110 01110011 01110101 01101100
--
From: . <.@gmail.com>
295424 294913 295424 294913 32768 294985 299016 294977 294913 299072
33344 32768 295489 295497 299016 294977 32768 299008 295488 294977
294913 299017 294977 33352 32768 33345 32768 294976 294977 299016 32768
295433 295497 295496 299017 299073 295488
--
From: Konsul Gnadenwalze <gnadenwalze@gmail.com>
%68%74%74%70%3a%2f%2f%69%6d%67%75%72%2e%63%6f%6d%2f%34%39%53%67%68
----
From: Danny van der Kleij
I just find it very strange that gmail marked it as "important because
of people in the email converstation" while I have never been emailed
by you before, which means you could use gmails "important" tag to
figure out who is in the bcc
----
From: Catarina Oliveira
??????????????????????????????????
----
From: Alisa Heller
Haha? What s this?
Other prototypes
In order to engage with email spam I have made few prototypes, so that I'd gain more insight into it. They consisted in:
- Archive of Spam email - soon to be put online
- Email exchanges with Mr. Wang, a banker in China who asked for my help in order to release a large sum of money frozen in his bank
General Work Methodology
The methodology I have employed in the constructions of my works generally begins by encountering a problem or frustration. I come across something in which I see potential, but due to some blockage, it is under-explored. As an example, I found a great wealth of audio material available at Internet Archive, however its interface tended to conceal most of the material. This frustration led me to ask how could the diversity and quantity of material become more apparent and accessible.
A stage of experimentation and research generally follows. At this point I try to broaden my question, find possible angles to approach it, find other approaches to similar problems, engage with my subject and experiment. The engagement with the subject seems crucial, it is a step towards the object of research, into trying to look at it closely, and to establish a dialog with it. This happen more clearly in Data Factory where I tried to convince direct-marking companies' employees into talking with me and answer my questions about direct-marking and users' privacy.
The following stage is one of concretization of the elected approach, bringing it from its experimental stage, through various prototypes to its final from. It is at this point when most decisions are made, such as what to include, in what context should it exist, how it will function, and what will be its material presence.
The resulting object is rarely, a solution for the problem which initiated the work process. Rather than providing an answer it will be an imaginative solution that ought pose more questions, show the problem under another, perhaps unexpected, perspective. Hopefully such approach will challenge the value of the object in question, and allow it to reveal itself under another form.
Description of my previous works in the past year
To begin with I started by writing on the performativity of code. Departing from Katherine Hayle's notion of code performativity I went on looking at how does code perform. How does code, rather than being a descriptive tool, has the capacity to act, to change things in the real world, similarly to a performative speech-act, such as a judge stating: "I pronounce you guilty of the crime", and often with more direct and material effects.
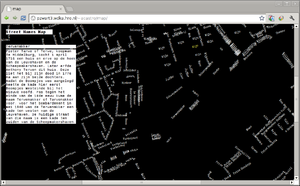
Simultaneously I developed and online map of the streets of Rotterdam. This map - a striped-down version of the original map of Rotterdam - only displayed the city street names against a black background, on the browser. By clicking on each street a request was made to the City of Rotterdam's Archive to provide information on that particular street's name origin. That information was then displayed alongside the map. What I seemed to be creating here was an interface to access city's archive through a different channel. By having the indexes of the archive - the street names - displayed on the screen I might see and ask for information on streets that I wouldn't normally be interested in. It opened up the possibility for a serendipitous navigation through the city history.
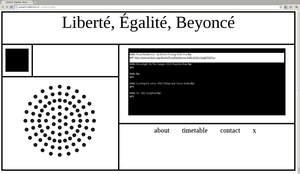
The same serendipitous exploration made its way to the next project, [Radio Liberté Egalité Beyoncé (RLEB)]. RLEB was an online radio-station with a schedule composed of audio content fetched form Internet Archive. One-hour long cycles presented the listener with ten-minutes chunks of various sound materials, picked at chance from the archive, within a specific categories, such as french talk-shows, hiphop, poetry readings, ambient music, etc. The design of website where RLEG was hosted presented a drawing of radio, with which the listener had to interact in order to get the radio playing.
The essay written alongside the RLEB began by tracing the archive's historical ties to power, functioning as a legitimator of power and knowledge. It mentioned the ideology which underlies any archive, even folkloric archive such as Youtube, an which can be best perceived through what is kept from entering the archive. Never-the-less important differences exist between a physical offline archive and a digital online one: the latter has the potential of a wider access, and also to let its item be taken by visitors, without the risk of impoverishment. These differences result in an invitation for appropriation of the digital archive. When one of its items is taken and transformed, a new version of it appears, and a certain confusion emerges over its origin - which one is the original and which is fictitious? When remixed versions surface, they change the archive into a space of dialogue and emergence of discourses, rather than a site for safekeeping and knowledge legitimization.
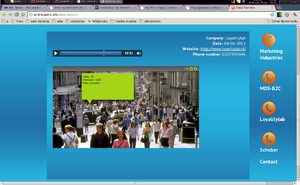
Data Factory looked at direct marking companies' acquisition of consumers data. It consisted of a small archive of recordings of phone-calls made to such companies. During the calls I tried to sell them their business's main ingredient - consumer data - with the catch being that "consumer" in this context meant only myself. Through the reactions to this simple short-circuit the ideology behind such business model became more apparent. The calls were gathered on a website, with a certain corporate style, in which they could be listened to, in parallel with images illustrating or ridiculing what was being said.
The essay The Work of Audiences departed from Dallas Smythe's text On the Audience Commodity and its Work. In Smythe's view, the audience job consists in creating demand for advertised goods. What advertisers buy when placing an advert on a magazine, TV-show of website is the audiences' attention and their capacity to buy what is being advertised. It happens that the labor of this immaterial work-force changed under the Web 2.0, as noted by Andrejevic. Audiences are no longer simply asked to generate demand for advertised goods, but also to put their creativity to work in producing many of the contents that surround those adverts. By doing so audiences also develop a community around their creations, and produce information about their behavior, which will be used in targeted advertisement directed at them. In exchange audiences receive a small amount of control over their creations, which are ultimately property of the company hosting them. Following this line of thought I asked whether there was a difference from the work of audiences on platform like Youtube to one like Wikipedia. The situation seems to be that although Wikipedia relies on audiences' free creative labor, they are given more control over their creations, and engage in discussions over the functioning of Wikipedia. Is this difference enough for the work of audiences to be classified as less exploitative than the one done for Youtube?